Identity-based attacks pose one of the gravest threats to information security systems. These attacks exploit and manipulate identities to breach systems or gain access to sensitive information. With the advent of modern technologies and the shift towards cloud computing, the significance of identity-based attacks has increased exponentially. In light of this, it is crucial for companies and organizations operating in the field of information security to prioritize robust protection by implementing zero-trust security.
Join us in this article to learn more about this security paradigm.
What is zero-trust security?
Zero-trust security is a security approach centred around the concept that organizations should not automatically trust anyone within or outside their perimeters. Instead, it emphasizes the importance of verifying the authenticity of identities, utilized resources, or any user attempting to access the system. Within this framework, all users and entities seeking network access must be authenticated and authorized before accessing any data or applications. These security measures should not end once users gain network entry; regular user monitoring and identity verification should be routine practices.
How does zero-trust security work?
Zero-trust security is achieved within an organization through various techniques, including continuous and recurrent user identity verification without the need for traditional passwords or authentication codes. Modern authentication techniques are employed when accessing a system or application protected by zero-trust security. User identity is established through multiple factors, such as device information and user location. Once the identity is verified, access to the system is granted.
- The operational mechanism of zero-trust security may include techniques like voice recognition, fingerprint scanning, and others to determine user identity.
Steps to Establishing Zero-Trust Security
- Identify users, services, and critical network data. This helps prioritize security policies and data protection by defining the important elements that require safeguarding.
- Understand the users utilizing privileged accounts and control who connects to what: Real-time visibility enables better control and ensures that all connections are based on trusted identities.
- Continuously verify access requests: Implement continuous verification of all access requests, regardless of the user’s initial entry.
Benefits of Implementing Zero Trust Security for Organizations
- Zero-trust security offers several advantages for organizations, including:
Reduced risk of breaches and manipulation of sensitive information.
Improved user experience with faster and easier access to systems and applications.
Enhanced security and effectiveness compared to traditional techniques.
- Zero-trust authentication has become one of the best practices in response to the evolving risks and challenges posed by cybersecurity threats. Many organizations have recognized the application of zero trust in addressing recent waves of security threats and successful ransomware attacks.
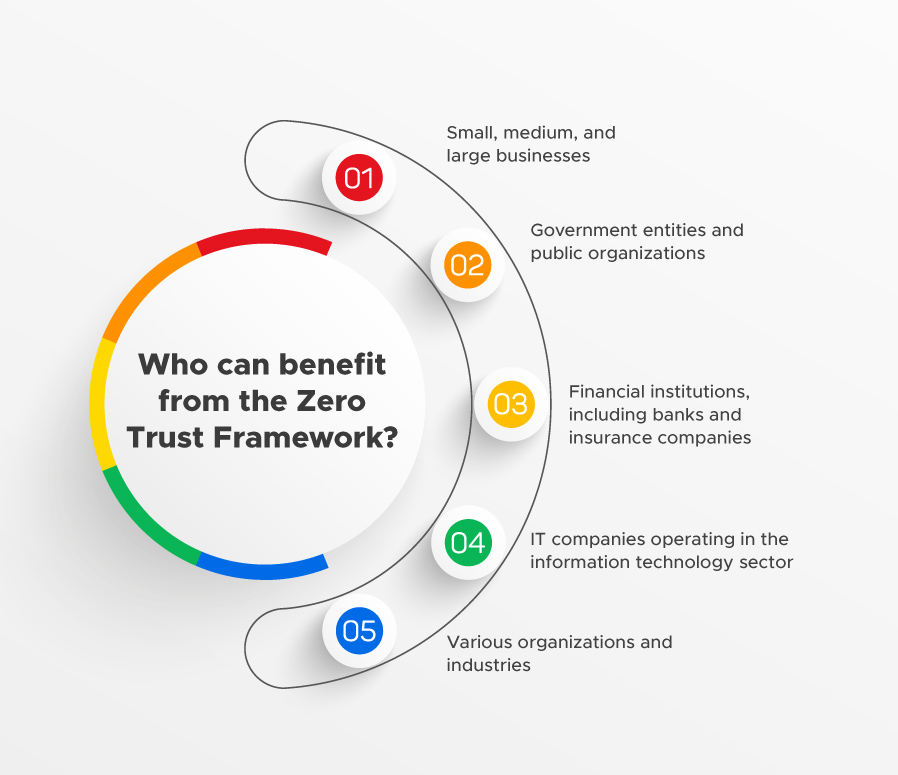
Who can benefit from the Zero Trust Framework?
- Small, medium, and large businesses
- Government entities and public organizations
- Financial institutions, including banks and insurance companies
- IT companies operating in the information technology sector
- Various organizations and industries
In conclusion,
it is crucial for organizations and entities to take appropriate security measures and implement the necessary approaches to protect themselves from electronic attacks. By consulting trusted companies and cybersecurity experts, you can identify the best security strategies tailored to your needs. Renad Al-Majd Technology Company is a leading information technology company in Saudi Arabia that offers a wide range of cybersecurity services and consultations..