The use of social media is no longer limited to normal people, but these means become the major platform that official bodies and organizations rely on it within the Kingdom for some jobs such as contacting their beneficiaries.
The presence of the official authority account within social media is very important and beneficial for business in general, but in case these accounts are somehow stolen or misused or the potential of impersonation of these bodies through social media it poses a great danger, Hence and to minimize these risks and preventing this danger, the idea of preparing Organizations’ Social Media Accounts Cybersecurity Controls for the official authorities (OSMACC-1-2021L) by the National Cybersecurity Authority (NCA) in the Kingdom, that clarifying the minimum of cybersecurity requirements to enable these parties to use social networks securely.

What’s the importance of Social Media Accounts Cybersecurity Controls?
The importance Of implementing the entity’s Social Media Accounts Cybersecurity Controls (OSMACC-1- 2021) is represented in:
- Contribute to raising the level of cybersecurity to the national level.
- Help to enable entities to use social media networks more securely.
- Implementing controls help to initialize entities to be prepared to face any potential cyber attack, which could lead to catastrophic consequences for that side.
The scope of implementing Organizations’ Social Media Accounts Cybersecurity Controls
These controls are implemented according to the National Cybersecurity Authority to the following entities when using social media.
- The government Entities in the Kingdom of Saudi Arabia and includes ministers, agencies, institutions, and others and its subsidiaries and affiliates.
- Private Sector entities that own, operate or host a sensitive national infrastructure.
The components of Organizations’ Social Media Accounts Cybersecurity Controls
Organizations’ Social Media Accounts Cybersecurity Controls consist of: 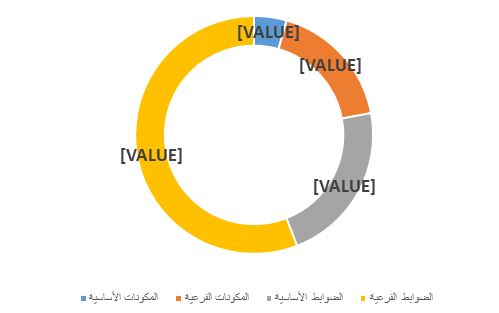
- 3 main domains.
- 12 subdomains.
- 15 main controls.
- 38 sub-controls.
- Cybersecurity Governance: It includes these subcomponents that works according to the organizational business requirements of the entity and related regulatory and legislative requirements.
- Cybersecurity policies and procedures: To ensure, document, approve and disseminate cybersecurity requirements and the entity’s commitment to them.
- Cybersecurity risk management: Systematically insurance of cybersecurity risks management and protect the entity’s information and technical assets.
- Cybersecurity in human resources: To ensure that the cybersecurity requirements and risks that related to the entity’s employees are treated effectively before, during, and at the end of their work.
- Cybersecurity Awareness and Training program: To ensure that the entity’s employees have the necessary security awareness, and they’re aware of their responsibilities in the field of cybersecurity, and to ensure that the entity’s employees are provided with the skills, qualifications, and training courses required in the field of cybersecurity to protect the information assets.
- Cybersecurity Defense: It includes these subcomponents:
- Assets management: To ensure that the entities has an accurate and up-to-date inventory of assets in order to support the entity’s operational process and cybersecurity requirements to achieve the confidentiality, safety, accuracy, and availability of the entity’s information and technical assets.
- Identity and access management: To ensure protecting cybersecurity for logical access to the entity’s information and technology assets in order to prevent unauthorized access.
- Information system and processing facilities protection: To ensure the protection of systems and information processing devices including users’ devices and the entity’s infrastructure from cyber risks.
- Mobile devices security: To ensure the protection of the entity’s mobile from cyber risks, and ensure the safe dealing with the entity’s sensitive and private information and protect it during the transportation and storage when using the personal devices of the entity’s employees.
- Data and Information protection: To ensure confidentiality, safety, accuracy, and availability protection of entity’s data and information.
- Cybersecurity Event logs and monitoring management: To ensure gathering, analyzing, and monitoring of the cybersecurity records at the appropriate time for proactive detection of cyber attacks and manage their risks to prevent to reduce the effects of the entity’s business.
- Cybersecurity incidents and threats management: To ensure determining and detection of cybersecurity incidents of the right time, and their effective management, and handling of cybersecurity threats proactively.
- Third-Party &Cloud Computing Cybersecurity: It includes this subdomain:
- Third-party Cybersecurity: To ensure the protection of the entity’s assets from third parties cyber-attacks according to the entity’s regulatory business requirements and the relevant legislative and regulatory requirements.