According to the kingdom’s vision to 2030, the enhancement of cybersecurity becomes very important to increase the trust in digitally and to secure the national infrastructure safety and endurance in different sectors, and because of considering communication, information technology, and the postal sector is one if the main structure of economic growth, where it supports the main competitive ability of national economy through high-speed broadband, electronic services, and information assets; communication and information technology commission has developed a comprehensive cybersecurity framework (CITC Cybersecurity Regulatory Framework (CRF)) aims to increase the level of maturity of cybersecurity in communication and information technology sector in the Kingdom of Saudi Arabia, the framework aims to:
- Organize and enable cybersecurity practices for the service providers in communication, information technology, and the postal sector.
- Raising the maturity level of cybersecurity in the communication and information technology sector.
- Adopt risk management methodology to achieve cybersecurity requirements.
- Ensure the confidentiality, safety, and availability of service provided to the customers.

The importance of implementing a CITC Cybersecurity Regulatory Framework (CRF)
The importance of implementing CITC Cybersecurity Regulatory Framework (CRF) is represented in:
- Saving time through providing a clear structure and methodology to take procedures related to cyber security.
- Determining weaknesses and shortcomings, to keep enhancing cybersecurity practices of communication, information technology, and Postal Service providers.
- Increase the level of trust in information technology, physical services, and assets to communication, information technology, and postal service providers.
- Processing monitoring and evaluating cyber security risks
- Use of security standards for software development.
- Consistency in the interpretation of security needs across different layers of work.
- The framework provides a common language and methodology to manage cybersecurity risks.
Compliance to regulatory and legislative requirements, Which opens new business avenues for the organization such as governmental entities, where working with them requires proof of the professionalism of your work, and the security of your information.
The scope of implementing CITC’s CRF framework
Implementing this framework rules on service providers in communication, information technology, and the postal sector they submission the authority as the regular of the sector and especially licensed service providers or registries to provide services.
Service providers in the communication and information technology sector are divided to:
- Service providers in the communication and information technology sector are classified as critical national infrastructure.
- Service providers in the communication and information technology sector are not classified as critical national infrastructure.
- Information technology and communication service provider licensed by the communication ad information technology commission.
- Postal service providers are licensed by the communication and information technology commission.
- Service providers in the communication and information technology sector are classified as critical national infrastructure.
- Service providers in the communication and information technology sector are not classified as critical national infrastructure.
Note: the authority is following up on the compliance f service providers with requirements and controls in different ways.
- Self-commitment models.
- Commitment workshops.
- Field inspections.
- Proactive or reporting audits.
CITC Cybersecurity Regulatory Framework (CRF) stages:
First: Before the cybersecurity regulatory framework enters into implementation.
- Generalize cybersecurity regulatory framework to service providers in communication, information technology, and the postal sector.
- Define service provider’s severity level through “determining service providers category form to determine the required compliance level”.
- Provide service providers with objectives to comply with the framework according to the level of risk.
- Evaluating the reality assessment model for measuring cybersecurity maturity level.
Second: After the CITC Cybersecurity Regulatory Framework enters into implementation.
- Generalize enters the framework into implementation to service providers in communication, information technology, and postal sector dated 30/5/2021.
- Request ”self-assessment to measure service provider compliance to cybersecurity requirements” during 20 working days of enters into implementation.
- The authority carries out audits and inspections to some of service providers according to self-assessment analysis results.
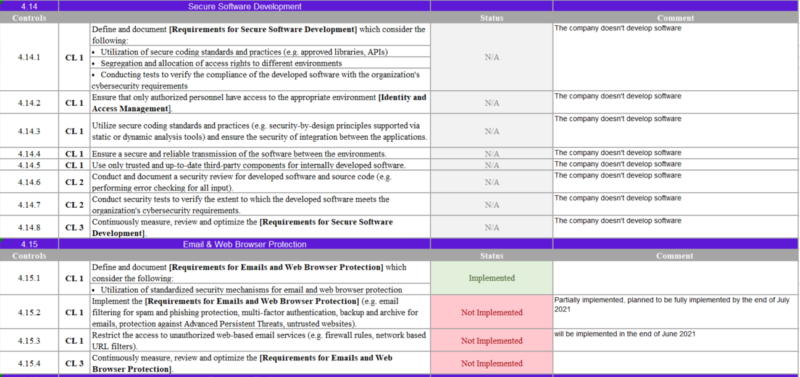
The component of the CITC Cybersecurity Regulatory Framework (CRF)
Requirements Structure table consist of:
- Department number.
- Department.
- Control number.
- Control
- Compliance level: include three levels in controls requirement which it:
- Level 1: includes the basic controls.
- Level 2: includes advanced requirements
- Level 3: includes requirements that are focusing on efficiency monitoring and contentious improvement to the controls in levels one and two.
References.
Renad AlMajed company Was able to be one of the earliest companies that implement a CITC Cybersecurity Regulatory Framework (CRF) for service providers in the communication, information technology, and postal sector Because of the group of experts and consultants it has who work with professionalism and dedication, the company provide many services, such as:
- Gap analysis, maturity assessment, and penetration test.
- Design, develop, implement and operate appropriate security quality systems for your organization.
- Make a comprehensive audit and review to your organization’s cybersecurity situation.
- Develop and formulate a cybersecurity strategy for your organization.
- Training and recruiting security cadre, and establishing an internal cybersecurity office and department.
- Providing awareness campaigns and training courses of cybersecurity that aim of knowledge transportation and enhancing their employee’s skills.
- Implementing a cybersecurity regularity framework for service providers in communication, information technology, and the postal sector.
- Audit and review quality systems, and ensure their compliance with regularity and legislative requirements.
- Insulting and operating security solutions (physical and electronic).
- Develop and implement an appropriate security incident response methodology, and security reporting system.
- When you ask for Renad AlMajed services, you are allowed to benefit of more than 60 experts and consultants in the fields of cybersecurity, information technology, and ISO standards.
- The company is characterized by flexibility, and the accuracy of implementation, and results show quickly, because of the awareness of the deep dimensions axes and indicators mentioned in the document.
- An expert team in a vulnerability assessment.
- Long experience of a penetration test.
- Security incidents need a quick reaction, and because of that, we have an operation center that works 24/7 to provide the appropriate support all-time without interruption.
- Working based on transparency, we provide an integrated and clear work plan, that involves a budget, schedule, and working mechanism before start implementing the project.
- High standards in providing services and customized the framework based on business needs.