IT or information security officials who attend to move toward the cloud must think many times before moving, the information security is very important to think about before moving to cloud services, and many other questions must be asked, such as:
- Am I secured?
- How to be sure I am secured?
- How to monitor and evaluate the security degree I have?


Many companies around the globe have private cloud hosting, that protects the data stored on it, but just relying on it is not sufficient for any person working in the information security field, as the following must be provided:
- A tool
- A software
- A framework
- A Standard
And that’s to monitor security degrees and governance in the cloud computing era.
It was created as an initiative that aims to increase transparency in the execution of security practices of cloud services providers worldwide. It combines the right mix of cloud controls that enables the evaluation of cloud services in accordance with PCI DSS, ISO 27001, NIST SP800-53, COBIT, HIPPA, BITS, FedRAMP, GAPP, and other international standards.
Cloud Security Alliance (CSA) Security Trust & Assurance Risk (STAR) can be considered as one of the most powerful programs for ensuring cloud services security, it combines the key principles of transparency, rigorous auditing, and harmonization of standards.
Security Trust Assurance and Risk (STAR) can assure transparency in security dealing, that is compatible with world standards, and the ability to be audited from any auditor and any specific part.
organizations who use STAR program indicate best security practices and security validation for their cloud computing products offerings across the world, CSA STAR program offers that all registry document ensures privacy and security for any controls which are used according to the cloud computing standards, This registry gives the necessary tools and references for any customers who is thinking in using cloud services to evaluate any security provider before committing with him and helps him to make the best decisions.
- Self-Assessment
Is a complimentary offering that documents the security controls provided by various cloud computing offers, thereby helping customers assess the current or recent security of cloud services providers.
Organizations can make Self-Assessment on security and privacy, then they can submit it to any company that uses Cloud services Controls Matrix for organization asset to evaluate their controls and document them:
- Frequency of Self-Assessment
STAR Self-Assessments are updated annually.
- customer visibility
Cloud services providers submit a completed Consensus Assessments Initiative Questionnaire (CAIQ) to document compliance with the Cloud services Controls Matrix (CCM), then this document becomes publicly available, which promotes industry transparency and provides customer visibility for specific providers security practices.
The published document ensures to save the confidentiality of sensitive information to avoid any exposure of information, the privacy assessment submissions are based on the GDPR Code of Conduct.
- General Data Protection Regulation (GDPR) Code of Conduct CoC Self-Assessment:
Voluntary publication on the STAR Registry consists of two documents:
- Code of Conduct Statement Adherence
- PLA Code of Practice (CoP) Template – Annex 1 self-assessment results
The Self-Assessment Code covers the compliance to GDPR of the service(s) offered by a content security policy CSP. After the publication of the relevant document on the Registry, an organization will receive a Compliance Mark valid for 1 year.
The Self-Assessment shall be reviewed every time there’s a change to the company policies or practices related to the service under assessment.
The Level 2 of STAR allows organizations to create other industry certifications and standards to make them specific for the cloud.
- Third-Party Audit:
Organizations can choose security and privacy audits and certifications from any third-party company audit. Each organization is different in location and some standards, roles, regulations may apply to this organization so it’s important to choose a third-party company that wears these standards, roles, regulations.
- CSA STAR Attestation
CSA, STAR program Attestation is a collaboration between CSA and the AICPA to provide guidelines for CPAs to conduct SOC 2 engagements using criteria from the AICPA (Trust Service Principles, AT 101) and the CSA Cloud services Controls Matrix.
STAR certifications provide for rigorous third-party independent assessments of cloud providers.
- The Duration of Attestation listings
The attestation duration will be one year unless updated.
- CSA STAR Certification
The CSA STAR Certification is a third-party accurate and independent assessment to secure a cloud service provider. The technology-neutral certification leverages the requirements of the ISO/IEC 27001:2013 Information Security management system standard together with the CSA Cloud Controls Matrix.
Certification certificates follow normal ISO/IEC 27001 protocol and expire after three years unless updated.
- GDPR Code of Conduct Certification
The GDPR, CoC Certification is a third-party certification assuring compliance of a CSP’s services to GDPR based on the CSA Code of Conduct for GDPR.
After the publication of the relevant document on the Registry, a company will receive a Compliance Mark valid for 1 year. The Self-Assessment shall be revised every time there’s a change to the company policies or practices related to the service under assessment.
It’s an automated process, where the cloud service provider automates the current security practices, and security practices for providers published to the public, each customer or vendor using a tool can capture the provider’s security practices that have been published.
A CSP, who holds a third-party certification or attestation can achieve STAR Level 2 Continuous by adding a Continuous Self-Assessment as in STAR Level 1.
The assessor will also ensure that the scope of the assessment includes STAR Continuous and assess the CSP’s submissions of the CAIQ over the term from the previous surveillance or re-certification visit.
For STAR Attestation, a Limited Assurance Report will be conducted to bridge the period between 2 attestation reports and provide a narrative in the audit report regarding the activities performed by the assessor that confirms the CSP met the STAR Continuous requirements.
CSA STAR Level 3
Full Cloud Services Assurance and Transparency If your organization operates in a high-risk environment, then we recommend pursuing STAR Level 3.
The CSP is the most transparent through a continuous, automated process that guarantee’s that security controls are monitored and validated at all times. Each control framework consists of multiple controls, which are designed to give assurance on the fulfillment of a requirement.
When preparing for continuous auditing, each one of those controls will be described via its characterizing objectives namely Service Level Objective (SLO) and Service Qualitative Objective (SQO).
The collection of data is driven by the metric that has been chosen to provide input about an attribute. Automated assessment is mostly driven by monitoring tools like log analytics, network statistics, and monitoring, process statistics, or resource utilization.
In the evaluation phase, the compliance status with the certification goal is determined by evaluating the controls. The result of the evaluation will be published and affirmed according to the targeted level of assurance by a third party. A certificate will be the result of this issue.
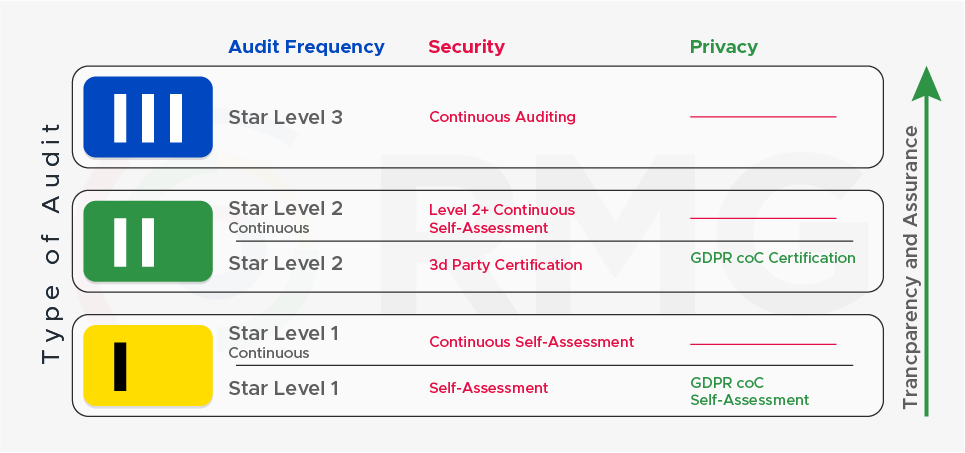
Each level of STAR has also had a continuous auditing option that allows you to increase your transparency. STAR Continuous can be attained by building upon the CSP’s current STAR level.
STAR Level 1: A CSP that uses a CAIQ to achieve Self-Assessment, and it’s a point-in-time assessment, can use a Continuous Self-Assessment to demonstrate the effectiveness of controls over a while, to achieve STAR Continuous Level 1.
STAR Level 2: A CSP, who holds a third-party audit, can achieve STAR Level 2 Continuous by adding a Continuous Self-Assessment, which allows them to quickly inform customers of changes to their security programs, instead of communicating those until the next audit period in normal STAR Level 2.
STAR Level 3: A CSP is the most transparent through a continuous, automated process that ensures that security controls are monitored and validated at all times.
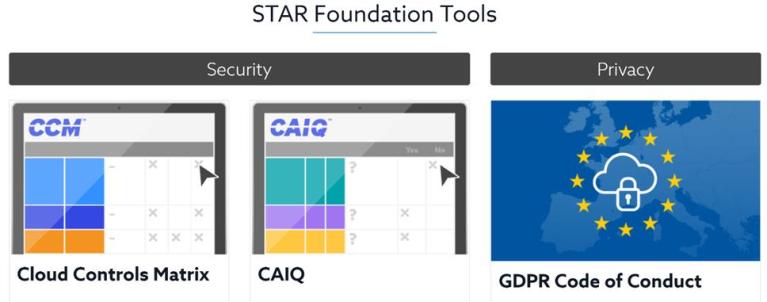
Cloud Controls Matrix (CCM)
The CSA, Cloud Controls Matrix (CCM) is a cybersecurity control framework for cloud computing, this framework consists of 133 control objectives that are cover 16 domains related to cloud technology.
Any customer can use CCM as a tool for cloud implementation assessment, also CCM provides guidelines to choose security controls during the implementation.
CCM framework complies with the Security Guidance v4 and is considered a standard for cloud security assurance and compliance.
The standards, Regulations & Controls Frameworks Map:
The controls in the CCM are mapped against industry-accepted security standards, regulations, and control frameworks including but not limited to: ISO 27001 /27002/27017/27018, NIST SP 800-53, AICPA TSC, ENISA Information Assurance Framework, German BSI C5, PCI DSS, ISACA COBIT, NERC CIP, and many others.
Consensus Assessment Initiative Questionnaire (CAIQ) v3.1
Consensus Assessments Initiative Questionnaire (CAIQ) v3.1 is presented by Cloud Security Alliance (CSA).
To choose any security controls in IaaS, PaaS, and SaaS services, CAIQ gives a simple document to make it easy to choose any controls that will be applied.
CAIQ consists of a set of Yes/No questions that appear in the customer or auditor’s mind before deciding which cloud service provider to choose and to be sure that its compliance with the Cloud Service Controls Matrix (CCM).
CAIQ can help customers to be sure that the security provided by service providers is enough and their data is protected and secured.
What is a GDPR Code of Conduct?
European General Data Protection Regulation (EU GDPR) was enforced recently, GDPR code of Conduct contains all requirements to comply with the EU GDPR that cloud service providers must satisfy.
This GDPR code of Conduct was created through coordination from a representative from the EU national data protection authorities, this GDPR code of Conduct helps organizations to adhere to the European General Data Protection Regulation.