In today’s interconnected digital landscape, where businesses rely heavily on technology and data, ensuring robust cybersecurity measures is paramount. Cyber threats are evolving at an alarming rate, and companies must take proactive steps to safeguard their digital assets and protect sensitive information, especially with the growing importance of personal data protection. The value of digital assets, particularly sensitive personal data, has never been higher, making cybersecurity and data protection critical imperatives for organizations of all sizes. As technology evolves, so do the methods employed by cybercriminals, necessitating a proactive and comprehensive approach to safeguarding digital landscapes.
This comprehensive guide aims to illuminate the path toward robust cybersecurity practices and compliance with the Data Protection and Cybersecurity Code (DCC). By exploring key principles and best practices, we empower businesses to fortify their defenses, mitigate risks, and uphold the trust of their clients and stakeholders. In an age where data is both a strategic asset and a potential liability, understanding the intricacies of cybersecurity and personal data protection is not just a choice; it is an essential commitment to the integrity and resilience of your digital enterprise. Join us on this journey as we delve into the crucial strategies and frameworks that form the foundation of a secure, responsible, and forward-looking approach to safeguarding your digital assets.
Personal Data Protection: Understanding the DCC
One of the key frameworks guiding personal data protection is the Data Protection and Cybersecurity Code (DCC). This comprehensive set of regulations outlines the necessary steps companies must take to secure personal data and mitigate the risks of cyber threats. Compliance with the DCC is not only a legal requirement but also a crucial step in building trust with customers and stakeholders.
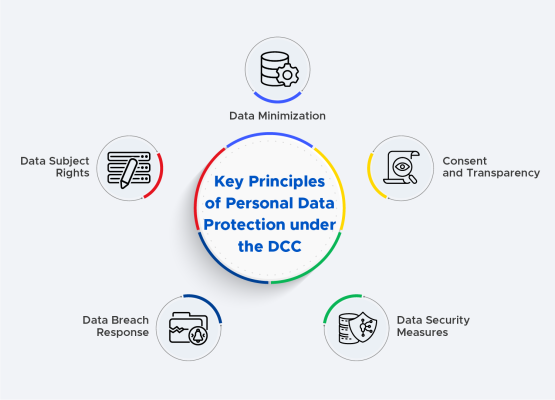
Key Principles of Personal Data Protection under the DCC
- Data Minimization: Collect and process only the data that is necessary for your business operations. Minimizing data reduces the risk associated with handling sensitive information.
- Consent and Transparency: Obtain explicit consent from individuals before collecting their data. Clearly communicate how the data will be used, ensuring transparency in data processing practices.
- Data Security Measures: Implement robust security measures to protect personal data from unauthorized access, disclosure, alteration, and destruction. Encryption, secure access controls, and regular security audits are essential components.
- Data Breach Response: Develop a comprehensive plan for responding to data breaches. Timely and transparent communication, along with swift action to contain and remediate the breach, is crucial to minimize the impact on affected individuals.
- Data Subject Rights: Respect the rights of data subjects, including the right to access, rectify, and erase their personal data. Establish processes to handle requests from individuals regarding their data.
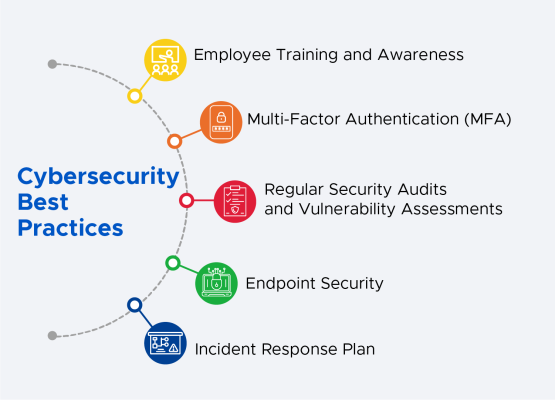
Cybersecurity Best Practices
In addition to adhering to the DCC, implementing robust cybersecurity practices is essential for safeguarding your company’s digital assets. Here are some key measures to consider:
Employee Training and Awareness: Educate your employees on cybersecurity best practices, including recognizing phishing attempts, using strong passwords, and understanding the importance of data protection.
Multi-Factor Authentication (MFA): Implement MFA to add an extra layer of security to user accounts. This significantly reduces the risk of unauthorized access, even if login credentials are compromised.
Regular Security Audits and Vulnerability Assessments: Conduct regular audits and assessments to identify and address potential vulnerabilities in your systems. Stay proactive in addressing security gaps before they can be exploited by cybercriminals.
Endpoint Security: Ensure that all devices connected to your network have up-to-date antivirus and anti-malware software. Regularly update and patch operating systems and applications to address known vulnerabilities.
Incident Response Plan: Develop and regularly test an incident response plan to ensure a swift and effective response in the event of a cybersecurity incident. This plan should include steps for identifying, containing, eradicating, recovering, and learning from security breaches.
In our increasingly interconnected world, the reliance on digital assets and the exchange of sensitive information have become intrinsic to the fabric of modern business operations. As organizations digitize their processes and embrace technological advancements, the need to fortify defenses against cyber threats has never been more pressing. “Safeguarding Your Digital Assets: A Comprehensive Guide to Cybersecurity and Personal Data Protection” aims to provide businesses with a roadmap to navigate the complex landscape of cybersecurity and ensure the protection of personal data.
Safeguarding the Kingdom: Saudi Arabian Monetary Agency’s Robust Cybersecurity Measures
In an era dominated by digital advancements, the need for robust cybersecurity measures has become paramount, especially for financial institutions that handle sensitive and valuable data. The Saudi Arabian Monetary Agency (SAMA) stands as a beacon of cybersecurity in the Kingdom, employing cutting-edge technologies and strategies to protect the financial infrastructure from evolving cyber threats.
1. Importance of Cybersecurity in the Financial Sector
The financial sector is a prime target for cybercriminals due to the vast amount of sensitive data it manages, including financial transactions, personal information, and critical infrastructure. In Saudi Arabia, where the financial sector is a key driver of the economy, SAMA plays a pivotal role in ensuring the stability and security of the monetary system.
2. SAMA’s Cybersecurity Framework
SAMA has developed a comprehensive cybersecurity framework that encompasses both preventive and responsive measures. The framework is designed to detect and thwart cyber threats in real-time while also having mechanisms in place to respond swiftly in case of a security breach.
A. Advanced Threat Detection Systems
SAMA employs state-of-the-art threat detection systems that continuously monitor network traffic, identify potential threats, and mitigate risks. These systems utilize artificial intelligence and machine learning algorithms to adapt to new and evolving cyber threats, ensuring a proactive defense against sophisticated attacks.
SAMA employs state-of-the-art threat detection systems that continuously monitor network traffic, identify potential threats, and mitigate risks. These systems utilize artificial intelligence and machine learning algorithms to adapt to new and evolving cyber threats, ensuring a proactive defense against sophisticated attacks.
B. Collaboration with Global Cybersecurity Experts
Recognizing the global nature of cyber threats, SAMA collaborates with leading cybersecurity experts and organizations. This international cooperation allows SAMA to stay abreast of the latest threats, vulnerabilities, and best practices in cybersecurity, enhancing its ability to defend against emerging risks.
3.Continuous Training and Awareness Programs
SAMA places a strong emphasis on the human element in cybersecurity. Regular training programs are conducted for employees to keep them informed about the latest cyber threats and security protocols. This proactive approach ensures that the staff remains vigilant and capable of identifying and responding to potential security risks.
4.Regulatory Compliance and Standards
SAMA enforces strict regulatory standards and compliance requirements for financial institutions operating within the Kingdom. These regulations cover various aspects of cybersecurity, including data protection, incident response, and risk management. Financial institutions are regularly audited to ensure compliance with these standards, fostering a secure financial ecosystem.
5. Incident Response and Recovery
In the event of a cybersecurity incident, SAMA has a well-defined incident response plan in place. This includes isolating affected systems, conducting forensic analysis, and collaborating with law enforcement agencies to investigate and mitigate the impact of the breach.
6. Outlook
As cyber threats continue to evolve; SAMA remains committed to staying ahead of the curve. The agency invests in research and development to explore emerging technologies and innovative cybersecurity solutions. By adopting a proactive approach and leveraging the expertise of global cybersecurity professionals, SAMA aims to fortify the Kingdom’s financial sector against future cyber threats.
The Saudi Arabian Monetary Agency’s dedication to cybersecurity is a testament to its commitment to protecting the Kingdom’s financial infrastructure. Through a combination of advanced technologies, international collaborations, continuous training, and regulatory enforcement, SAMA stands as a guardian against cyber threats, ensuring the stability and security of the financial sector in Saudi Arabia.
In conclusion, as the threat landscape continues to evolve, companies must prioritize cybersecurity and personal data protection to maintain the trust of their customers and stakeholders. Adhering to the principles outlined in the Data Protection and Cybersecurity Code (DCC) and implementing robust cybersecurity measures will not only help your organization comply with regulations but also fortify your defenses against the ever-growing range of cyber threats. By investing in cybersecurity, you are not only protecting your company’s digital assets but also contributing to a safer and more secure online environment for everyone “Safeguarding Your Digital Assets” serves as a compass for businesses navigating the complex digital landscape. By adopting the principles outlined in this comprehensive guide, organizations can not only comply with regulatory requirements but also fortify their digital defenses against the ever-evolving threat landscape. In doing so, businesses can foster a culture of responsible data management, uphold the trust of their stakeholders, and confidently embrace the opportunities presented by the digital age.