Blog Body
Learn about the essential cybersecurity requirements needed to protect your organization’s data and systems. A comprehensive guide to implementing best practices and building a secure and reliable digital environment.
In today’s highly interconnected digital environment, digital information assets have become the lifeblood of organizations of all sizes and across all sectors. Sensitive data, critical operational systems, intellectual property, and customer interactions all rely on digital infrastructure. With the increasing cybersecurity challenges and threats, as previously discussed, merely being aware of the risks is no longer sufficient. It has become essential to activate tangible procedures and strategies that ensure the highest levels of protection. This requires adherence to a comprehensive set of cybersecurity requirements that form the foundation for any strong and effective digital defense posture. Understanding and implementing these requirements is not just about regulatory compliance, but a vital investment in business continuity, building trust with customers, and maintaining the organization’s reputation. In this article, we review the most prominent cybersecurity requirements that every organization needs to focus on to ensure a secure and resilient digital environment.
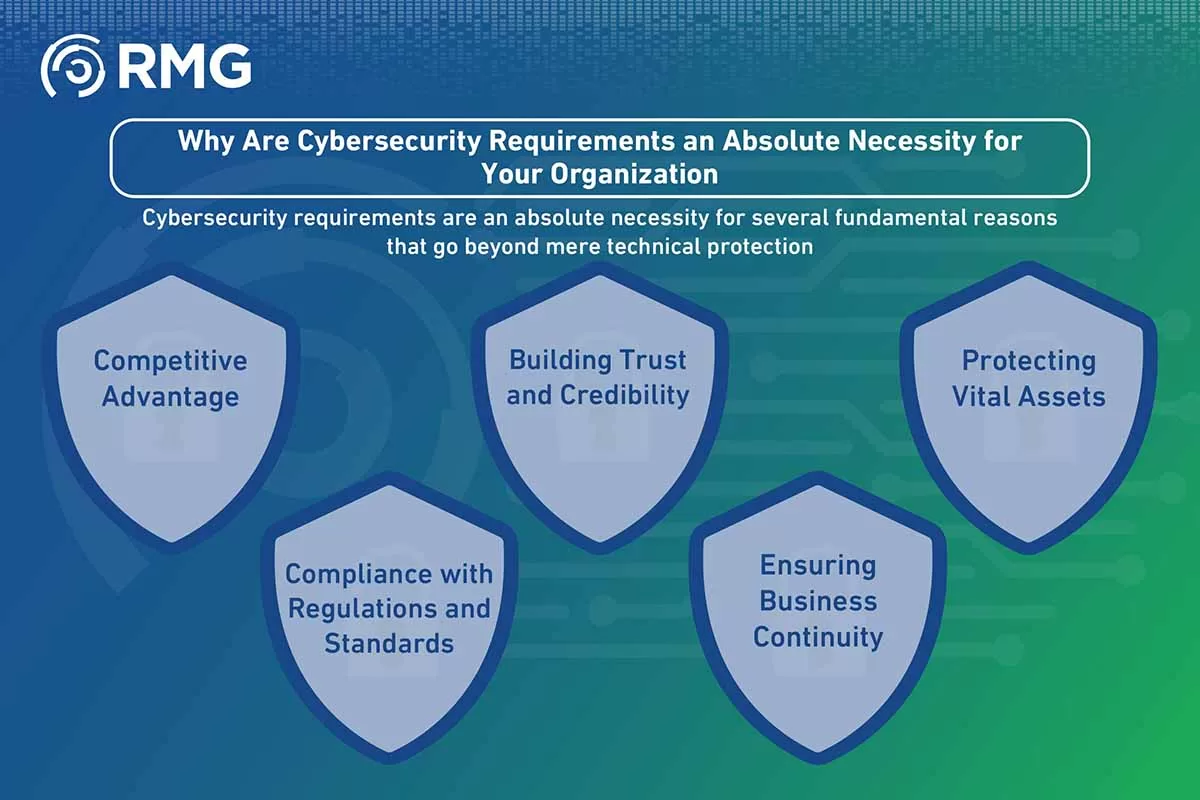
Why Are Cybersecurity Requirements an Absolute Necessity for Your Organization?
Cybersecurity requirements are an absolute necessity for several fundamental reasons that go beyond mere technical protection:
- Protecting Vital Assets: The requirements ensure the implementation of necessary measures to protect sensitive data, operational systems, and intellectual property from theft, damage, or unauthorized access.
- Ensuring Business Continuity: Adhering to cybersecurity requirements helps reduce the likelihood of devastating attacks that could lead to business disruption, and also ensures the existence of rapid recovery plans in the event of an incident.
- Building Trust and Credibility: Companies that respect cybersecurity requirements prioritize the protection of their customers’ and partners’ data, which enhances trust and builds a strong reputation in the market.
- Compliance with Regulations and Standards: Many industries and government bodies impose strict regulations for data protection and cybersecurity. Adherence to these requirements helps the organization avoid potential fines and legal penalties.
- Competitive Advantage: In an increasingly digital market, strong cybersecurity can be a unique selling point and a competitive advantage that distinguishes your organization from others.
The Three Foundations of Effective Cybersecurity Requirements: Policies, Technology, and People
Effective cybersecurity cannot be achieved by focusing on only one aspect. Cybersecurity requirements demand a comprehensive view based on three interconnected foundations:
- Policies & Procedures: Establishing rules and controls that govern how digital assets and information are used and managed.
- Technology & Tools: Using the necessary technical solutions to implement policies and provide technical protection.
- People & Awareness: Ensuring employees are aware of risks and policies, and empowering them to become the first line of defense.
These three foundations interact to form a robust security framework that covers all aspects of the organization’s digital environment.
Policy and Procedure Requirements: The Roadmap for Your Organization’s Security
Security policies and procedures serve as the constitution that governs the behavior of users and systems within the organization. Cybersecurity requirements in this aspect include:
- Acceptable Use Policy: Defines how the organization’s devices, networks, and systems should be used.
- Access Control Policy: Determines who can access which data or systems and with what level of privileges (principle of least privilege).
- Data Management Policy: Covers data classification, how it is stored, processed, transferred, and securely destroyed.
- Incident Response Policy: Defines the steps to be taken when a security incident is detected.
- Backup and Restoration Policy: Ensures regular data backups and procedures for quick restoration.
- Change Management Procedures: Ensuring that any changes to systems are security-evaluated before being implemented.
These policies must be clearly written, communicated to all employees, and reviewed and updated regularly.
Technical Requirements: Building the Strong Defensive Infrastructure
The technical aspect is a cornerstone in meeting cybersecurity requirements. This involves implementing a set of technical tools and solutions to protect networks, systems, and data:
- Firewalls: To control and filter data traffic between different networks.
- Intrusion Detection and Prevention Systems (IDS/IPS): To monitor traffic, detect suspicious activity, and respond to it.
- Endpoint Protection Platforms (EPP/EDR): To secure devices used by employees (computers, smartphones).
- Encryption: To protect data during transit and at rest.
- Multi-Factor Authentication (MFA): To add an extra layer of protection during login.
- Vulnerability Management: A regular process to identify and patch vulnerabilities in software and systems (Patch Management).
- Identity and Access Management (IAM): Centralized systems for managing user accounts and permissions.
- Security Information and Event Management (SIEM) System: To collect and analyze security event logs from various systems to detect and respond to threats.
Training and Awareness Requirements: Empowering the Human Element to Be the First Line of Defense
The human element remains the most important factor in cybersecurity, but also the most susceptible to social engineering and unintentional errors. Therefore, essential cybersecurity requirements include:
- Regular and Continuous Training Programs: To educate employees about the latest threats (such as phishing, malware) and how to recognize and avoid them.
- Awareness Campaigns: Using emails, posters, meetings to remind employees of the importance of cybersecurity and the established policies.
- Simulated Phishing Tests: Sending fake phishing emails to gauge employee response and identify those who need additional training.
- Integrating Security into the Organizational Culture: Making cybersecurity a part of the organization’s daily values and operations.
Continuous Assessment and Monitoring Requirements: Staying Vigilant in the Face of Changing Threats
Cybersecurity is not a static state, but a continuous process that requires vigilance and periodic evaluation. Cybersecurity requirements in this aspect include:
- Vulnerability Assessment: Scanning systems and networks to identify known weaknesses.
- Penetration Testing: Simulating real attacks to evaluate the effectiveness of security controls and identify exploitable vulnerabilities.
- Security Audits: Evaluating compliance with security policies, procedures, and regulatory standards.
- Continuous Monitoring: Using SIEM tools and monitoring systems to monitor network activity and detect any suspicious behavior in real-time.
- Log Analysis: Reviewing system and application logs for indicators of unauthorized activity.
Incident Response and Disaster Recovery Requirements: Preparing for the Worst to Minimize Damage
Despite the best preventive measures, security incidents can occur. Therefore, fundamental cybersecurity requirements include having ready plans to deal with these scenarios:
- Incident Response Plan (IRP): Clear documentation of the steps to be taken when a security incident occurs, including defining responsibilities, containment steps, investigation, and recovery.
- Disaster Recovery Plan (DRP): A plan to restore systems and operations after a major disaster (such as a widespread ransomware attack or infrastructure failure).
- Business Continuity Plans (BCP): Ensuring the organization’s ability to continue providing essential services during or after a major incident.
- Plan Testing: Conducting regular exercises and tests to ensure the effectiveness of the plans and the readiness of the concerned teams.
Compliance with Standards and Regulations Requirements: Adhering to Legal and Industry Frameworks
Compliance with relevant regulations and standards is an integral part of cybersecurity requirements for organizations. The type and level of required compliance vary based on industry and geographical region. Examples of frameworks and standards include:
- General Data Protection Regulation (GDPR): For handling data of European Union citizens.
- Payment Card Industry Data Security Standard (PCI DSS): For organizations that handle payment card data.
- ISO 27001 Standards: The internationally recognized information security management system.
- Frameworks such as NIST Cybersecurity Framework: A flexible and scalable framework for managing and reducing cybersecurity risks.
- Local Regulations: Such as the regulations of the Communications and Information Technology Commission (CITC) or the Saudi Central Bank (SAMA) in some countries.
Adhering to these standards not only protects the organization from penalties but also reflects its serious commitment to data protection and security.
Third-Party and Supplier Risk Management Requirements: Expanding Your Protection Scope
In the modern business world, organizations rarely operate in isolation. Data is often exchanged or systems accessed by suppliers, partners, or cloud service providers (third parties). Therefore, a critical cybersecurity requirement is to assess and manage the risks that may arise from these relationships:
- Security Assessment of New and Existing Suppliers: Ensuring they have adequate security measures to protect the data or systems they handle.
- Including Clear Security Requirements in Contracts: Defining suppliers’ obligations regarding cybersecurity.
- Regular Monitoring of Supplier Security Performance: Ensuring their continued adherence to the required standards.
Transforming Cybersecurity Requirements into Tangible Reality: Renad Majd’s Integrated Solutions
Meeting cybersecurity requirements is not a simple process; it requires careful planning, continuous investment, and a deep understanding of the evolving threat landscape. It is an ongoing journey towards building strong digital resilience.
Achieving these multiple and complex requirements can be a challenge for organizations, especially those lacking specialized expertise or sufficient internal resources. This is where the role of an expert partner comes in, who can guide the organization and help it meet these cybersecurity requirements effectively and efficiently.
Renad Majd Company fully understands the challenges organizations face in achieving full compliance with cybersecurity best practices and regulations. Therefore, we have designed a comprehensive suite of services and solutions to help our clients meet all the cybersecurity requirements they need. We provide specialized consultations to develop appropriate security policies and procedures, and we design and implement advanced technical solutions covering protection from the endpoint to the cloud. We also offer interactive training and awareness programs for employees and conduct regular assessments and penetration tests to identify and address vulnerabilities. Our goal is to empower your organization to build and implement a strong and robust security framework that ensures the protection of your digital assets and full compliance with regulatory requirements.
Your Partner Towards Uncompromising Digital Compliance and Security: An Invitation to Contact Renad Majd
We invite all entities and organizations that seek to strengthen their security posture and meet all necessary cybersecurity requirements to ensure a safe and reliable digital work environment to contact the Renad Majd expert team today. Let us help you assess your current situation, identify the most critical requirements for your needs, and design and implement optimal solutions that guarantee you security, compliance, and peace of mind. Do not let the complexities of cybersecurity hinder your progress.
Contact us now to benefit from our expertise and build a secure digital future for your organization, through the following form: