Consulting services
First: Obtaining licenses from the Space and Technology Communications Commission (CST)
Assist telecommunications or cloud service providers (LSPs) in obtaining the necessary license from the TRA through:
- Achieve minimum cybersecurity requirements, and comply with the regulations required by the Authority.
- Raising the levels of classification of companies in accordance with the levels approved by the Authority. CSP Registration Class (A, B or C)
- Conducting the necessary assessment of the Cybersecurity Regulatory Framework (CRF)
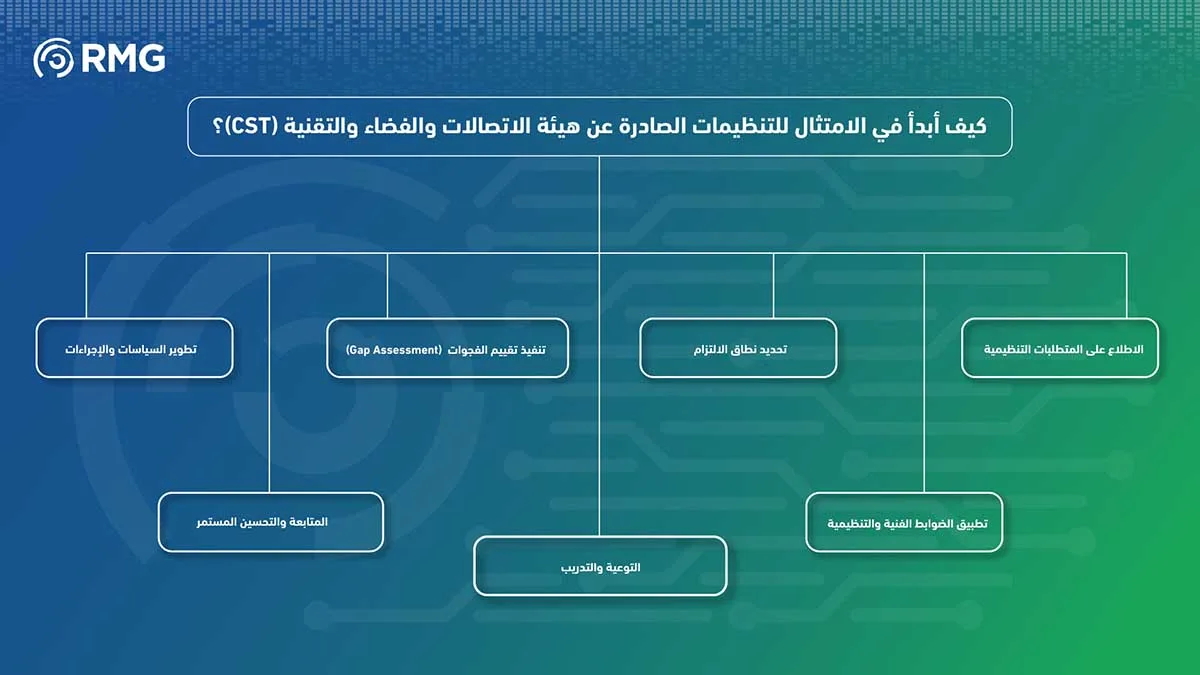
1. See regulatory requirements
- Cybersecurity regulatory framework for the ICT sector.
- Data Protection and Privacy Instructions.
- Licensing controls and the operation of technical and space services.
2. Define the scope of commitment
Identify activities and services of your entity that are subject to the Authority’s regulations (e.g. Internet services, infrastructure, cloud, satellite…) to apply only the relevant requirements.
3. Implement a Gap Assessment
Compare the current situation in the region with regulatory requirements to identify strengths and gaps.
Based on this assessment, an action plan is prepared to address the gaps and achieve full commitment.
4. Develop policies and procedures
Prepare or update the following policies to comply with the requirements of the Authority:
- Cybersecurity policy.
- Data Protection and Privacy Policy.
- Risk Management Policy.
- License Management and Operating Policy.
5. Apply technical and organizational controls
Implementing the required security and technical measures such as:
- Access and permissions management.
- Monitor security events and respond to incidents.
- Protect networks and systems.
- Periodic security updates.
6. Outreach and Training
Spreading the culture of compliance among the entity’s employees through periodic training and awareness programs on:
- The importance of organizations.
- Their responsibilities in their implementation.
- How to deal with data and cybersecurity.
7. Continuous Follow-up and Improvement
- Monitor security and compliance performance indicators.
- Perform periodic internal reviews.
- Submit compliance reports to the Authority upon request.
Second: Compliance Solutions for the Relevant Regulations and Legislations
1. ISO/IEC 27017 Cloud Information Security Certification
Assist in obtaining the ISO 27017 (Cloud Information Security) compliance certificate by providing the following consulting services:
Steps:
- Information Security Management System (ISMS) Scope:
Includes only cloud computing services (IaaS, PaaS, SaaS) and is strictly scoped to cover only cloud assets and systems. - Defining the Cloud Compliance and Governance Management Team:
Includes representatives from cybersecurity, IT, contracts, and governance. Defining Cloud Cybersecurity Governance roles and responsibilities.
- Identify Initial Gaps:
Analyze the current status of the entity against the requirements of ISO 27017 or NCA CCC.
Preparing the required documents and policies for ISO/IEC 27017 certification.
Required Core Documents and Policies:
- Cloud Information Security Policy
- Defines senior management’s commitments and responsibilities for data protection in the cloud environment.
- Reflects NCA CCC controls for Cloud Governance.
- Cloud Data Classification and Management Policy.
- Cloud Access Control Policy.
- Procedures for protecting information and ensuring its security during transmission and storage in the cloud.
- Security Service Level Agreements (SLAs) with the cloud service provider.
- Cloud Vendor Assessment Model.
 Steps:
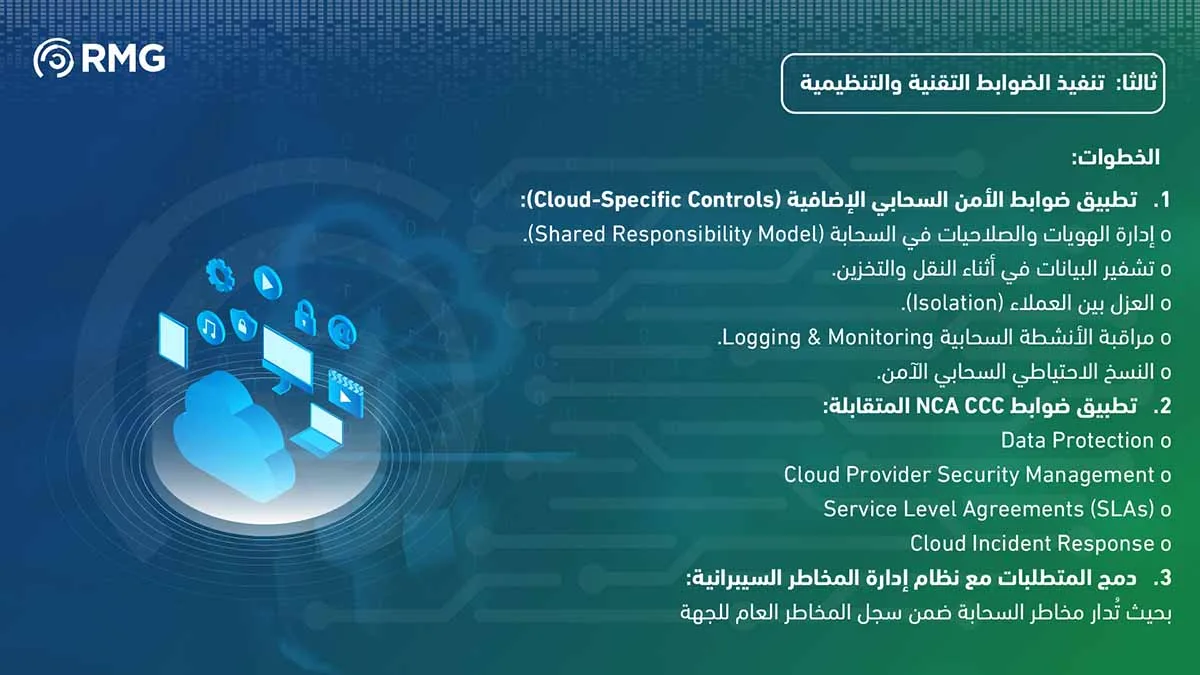
Implement additional cloud security controls:
… Monitoring.
Steps:
Implement additional cloud security controls:
… Monitoring.
- Data Protection
- Cloud Provider Security Management
- Service Level Agreements (SLAs)
- Cloud Incident Response
- Conduct an internal audit to verify compliance with ISO/IEC 27017 and 27001 controls
- Conduct a management review to present the results of the internal audit and the improvement plan.
- Address the identified observations and gaps.
- Choose an internationally recognized certification body (such as BSI, TÜV, Infinity)
- Submit the formal certification application (Stage 1 Audit): – Review the documentation, scope, and policies.
- Conduct the on-site audit (Stage 2 Audit): – Examine the effectiveness of the controls actually implemented in the cloud environment.
- Receive ISO/IEC 27017 certification.
- Annual follow-up (Surveillance Audit): To maintain the validity of the certification for 3 years.
2. NCA CCC Compliance
Compliance with the Cloud Computing Cybersecurity Controls Framework (NCA CCC – 2:2024) is carried out through an integrated methodology that goes through five main phases developed by the National Cybersecurity Authority, and is based on the linkage between CCC and ECC controls (core controls):
Steps:
- Define the scope of work and applicability
- Inventory of all cloud computing services (IaaS, PaaS, SaaS) used or provided by the entity.
- Specify the type of entity (cloud service provider/service subscriber).
- Identify and classify hosted data according to the approved data classification guide.
- Defining responsibilities
- Define cybersecurity roles and responsibilities within the RACI (Responsible, Accountable, Consulted, Informed) model.
- Adopting the cybersecurity governance of cloud computing within the general cybersecurity structure of the entity.
- Identify relevant technical and regulatory requirements
- Aligning the compliance plan with NCA CCC-2:2024 controls and relevant body decisions such as third-party controls and sensitive systems.
Steps:
- Conducting a gap analysis using the official assessment tool from the Authority.
- Evaluation of controls in the four main areas:
- Cybersecurity Governance
- Strengthening Cyber Defense
- Cyber Resilience
- Third-party cybersecurity and cloud computing
- Documenting the results in the compliance record and linking them to the NCA CCC controls matrix
Steps:
- Prepare a remediation plan that includes activities, priorities, and timeline.
- Implement core cloud computing controls, such as:
- Protect hosted data and separate virtual environments
- Hosting sensitive systems within the Kingdom
- Documenting and updating cybersecurity requirements for cloud computing and hosting services
Steps:
- Carry out periodic self-assessment of the applicable controls.
- Review your cloud computing and hosting controls periodically
- Documenting supporting evidence such as:
- Policies and procedures adopted.
- Cloud security test results.
- Independent audit or evaluation reports.
Steps:
- Submit compliance reports to the National Cybersecurity Authority (NCA) upon request.
- Update the annual improvement plan based on the results of assessments or any legislative changes.