Blog Body
Discover how secure cloud computing forms an impenetrable digital fortress for your organization. This is your comprehensive guide to the best strategies for securing cloud data and ensuring regulatory compliance in the Saudi market.
What is Secure Cloud Computing and Why is it an Absolute Necessity for Saudi Organizations?
At the heart of Saudi Arabia’s digital transformation, cloud computing is no longer just a digital option; it has become a fundamental driver of innovation and growth. However, with the increasing reliance on the cloud, a critical challenge arises: security. This is where secure cloud computing emerges, not as an add-on, but as a holistic and essential concept. It’s not just a collection of tools, but a comprehensive strategy and methodology aimed at protecting the data, applications, and infrastructure associated with cloud computing from both internal and external threats.
For government and private organizations in the Kingdom, secure cloud computing has become an indispensable necessity. With the growing volume of sensitive data—whether it’s citizen data, financial information, or trade secrets—any security breach can lead to severe consequences that go beyond financial losses to include reputational damage and a loss of trust. Adopting a proactive approach to cloud security ensures business continuity, enhances compliance with stringent local regulations imposed by bodies like the National Cybersecurity Authority (NCA), and enables organizations to fully leverage the flexibility and power of the cloud without jeopardizing their digital assets.
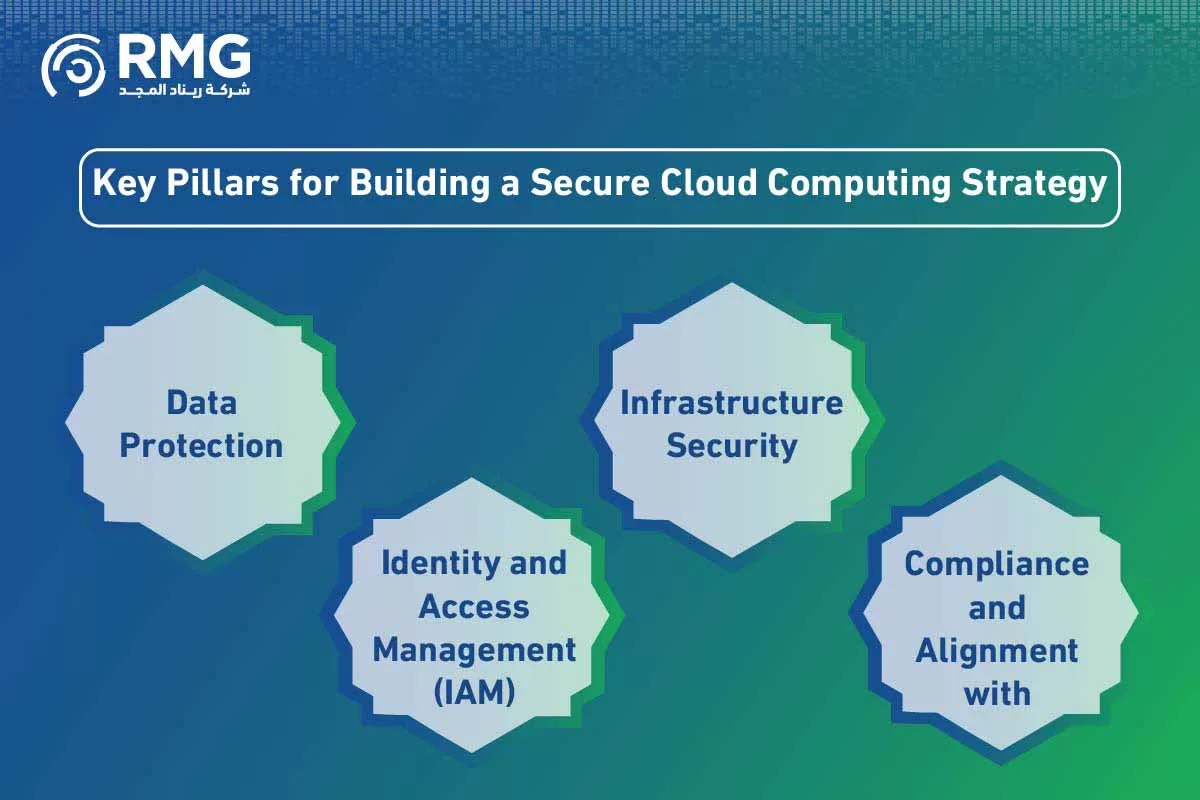
Key Pillars for Building a Secure Cloud Computing Strategy
Achieving cloud security isn’t a random process; it requires a strategic foundation built on several core pillars that work together to form a comprehensive digital shield. These pillars are the foundation of any successful secure cloud computing system.
Data Protection: Absolute Encryption at Rest and in Transit
Data is the crown jewel of any organization. Secure cloud computing starts by ensuring the confidentiality and integrity of this data throughout its lifecycle. This includes using strong encryption protocols for “Data in Transit” between the user and the cloud, as well as encrypting “Data at Rest” when it’s stored on cloud servers. This guarantees that even in the event of unauthorized access to the physical infrastructure, the data remains unreadable and unusable.
Identity and Access Management (IAM): Who Holds the Keys to Your Digital Kingdom?
Identity and Access Management (IAM) is the first line of defense. Most breaches occur due to weak permission management. Secure cloud computing requires the implementation of strict access policies based on the “Principle of Least Privilege,” meaning each user or system is granted only the necessary permissions to perform their tasks. Furthermore, enabling Multi-Factor Authentication (MFA) is a vital step to add an extra layer of security that protects accounts even if passwords are leaked.
Infrastructure Security: Fortifying Networks and Virtual Machines
While the cloud service provider secures the physical infrastructure, the organization is responsible for securing its own cloud configurations. This includes setting up Cloud Firewalls, segmenting virtual networks (VNet Peering/Segmentation) to isolate sensitive applications, and using Intrusion Detection and Prevention Systems (IDS/IPS) to monitor for suspicious activities and block them in real-time. A secure cloud infrastructure prevents attackers from moving horizontally within the network if they manage to breach a single point.
Compliance and Alignment with Regulations: Meeting the Kingdom’s Requirements
Regulatory bodies in Saudi Arabia, led by the National Cybersecurity Authority (NCA), are working to establish strict controls and standards to protect the national cyber landscape. Any secure cloud computing strategy must put compliance with these regulations at its core. This includes ensuring data sovereignty by hosting sensitive data within the Kingdom’s borders, implementing the Essential Cybersecurity Controls (ECC), and being able to provide periodic reports proving adherence to the required standards.
Best Practices for Implementing Secure Cloud Computing in the Saudi Business Environment
Transitioning to the cloud securely goes beyond simply purchasing technology; it requires adopting a security culture and implementing proven practices to ensure maximum protection.
Understanding the Shared Responsibility Model: Defining Roles and Responsibilities
A common mistake is believing that the cloud service provider is responsible for all aspects of security. The truth lies in the “Shared Responsibility Model.” While the provider is responsible for “Security of the Cloud”—the physical infrastructure and underlying networks—the organization is responsible for “Security in the Cloud.” This includes protecting data, managing access, securing applications, and configuring networks. Clearly understanding these boundaries is the first step toward building an effective secure cloud computing strategy.
Continuous Monitoring and Incident Response: The Vigilant Eye on Your Digital Assets
Cyber threats are constantly evolving, so it’s not enough to set up defenses and wait for an attack. Secure cloud computing requires a 24/7 continuous monitoring system. Using tools like SIEM (Security Information and Event Management) and having a Security Operations Center (SOC), organizations can collect and analyze activity logs from various cloud sources, identify suspicious patterns, and respond immediately to security incidents before they escalate.
Choosing a Trusted Cloud Service Provider: Non-Negotiable Criteria
Choosing the right cloud partner is a strategic decision that directly impacts the level of security. When evaluating providers, organizations in the Kingdom should look for partners with recognized global certifications (such as ISO 27001, SOC 2, CSA STAR), that provide local data centers to ensure data sovereignty, offer clear Service Level Agreements (SLAs) guaranteeing performance and security, and have a proven track record of providing secure cloud computing services to sensitive sectors like government and finance.
Renad Al Majd (RMG): Enabling Secure Digital Transformation in the Kingdom
In this complex landscape, Renad Al Majd (RMG) stands out as a leading strategic partner that doesn’t just offer digital solutions, but provides an integrated vision for achieving secure cloud computing. Renad Al Majd understands that the challenges facing Saudi organizations are unique and require a deep understanding of the local context and national regulations.
Renad Al Majd offers specialized consulting services that start with assessing the current security posture of a cloud infrastructure, identifying security gaps, and designing a fortified cloud architecture that is fully compliant with the NCA’s controls. Their team of experts relies on global best practices to implement the core security pillars, from designing Identity and Access Management policies and deploying advanced encryption solutions, to configuring secure networks and establishing incident response plans. RMG’s role goes beyond implementation to include empowerment, working to build internal capabilities for their clients to ensure long-term security sustainability.
Build a Secure Digital Future: Join Industry Leaders by Partnering with Renad Al Majd
The journey of adopting secure cloud computing is not just a technical project; it’s a strategic investment in an organization’s future. Choosing the right partner is the crucial factor that distinguishes between simply using the cloud and leveraging it as a secure and reliable platform for growth and innovation.
Renad Al Majd (RMG) invites all government bodies and public and private sector organizations in the Kingdom to begin a strategic partnership aimed at building a fortified digital future. By partnering with Renad Al Majd, your organization can move beyond mere regulatory compliance to achieve security excellence, allowing you to focus on your core business objectives with complete confidence that your digital assets are in safe hands. Don’t let security challenges hinder your digital transformation journey.
Contact the team of experts at Renad Al Majd today and discover how they can help you design and implement a secure cloud computing strategy that lives up to your ambitions and ensures your leadership in the digital age.