Blog Body
Discover how implementing cybersecurity governance can transform your digital defenses from mere procedures into a strategic asset. An expert guide for Saudi organizations to achieve compliance and excellence in the face of advanced threats.
Cybersecurity Governance: Not an Option, But a Strategic Imperative
At the heart of Saudi Arabia’s accelerating digital transformation, the view of cybersecurity is no longer limited to technical management or just a firewall. The concept has evolved to become an integral part of organizations’ overarching strategy. This is where the role of Cybersecurity Governance emerges. It’s not merely a set of policies; it’s the nervous system that directs, monitors, and manages all cybersecurity efforts within an organization, ensuring their full alignment with strategic objectives and the protection of valuable digital assets. It’s the framework that transforms cybersecurity from a reactive measure into a proactive action, and from a cost into a smart investment.
What is Cybersecurity Governance? A Definition Beyond the Ordinary
Cybersecurity governance is defined as the set of processes, organizational structures, and decision-making mechanisms through which an organization’s leadership (Board of Directors and Executive Management) ensures the direction and monitoring of cybersecurity activities to achieve the following objectives:
- Strategic Alignment: Linking cybersecurity objectives with the organization’s key business goals.
- Risk Management: Identifying, assessing, and addressing cyber risks in a manner consistent with the organization’s risk appetite.
- Value Realization: Ensuring that cybersecurity investments yield tangible returns by protecting assets and enabling business operations.
- Resource Management: Efficiently and effectively allocating human, technical, and financial resources.
- Performance Measurement: Continuously monitoring and evaluating the effectiveness of cybersecurity controls and programs.
Simply put, cybersecurity governance answers the fundamental questions: “Are we doing the right things?” and “Are we doing them the right way?” to ensure the security and continuity of our operations.
Why is Cybersecurity Governance a Cornerstone for Saudi Organizations?
In the dynamic Saudi business environment, implementing a robust cybersecurity governance framework is of paramount importance for several vital reasons:
- Compliance with National Regulations: The National Cybersecurity Authority (NCA) in Saudi Arabia sets stringent requirements and controls (such as the Essential Cybersecurity Controls – ECC) that all government and private entities must adhere to. Effective governance is the optimal way to ensure continuous compliance and avoid penalties.
- Protection of Critical Assets: Organizations today rely entirely on data and digital infrastructure. Cybersecurity governance provides the necessary oversight to protect these assets from increasing threats, whether internal or external.
- Enhancing Stakeholder Trust: Customers, investors, and partners place greater trust in organizations that demonstrate a clear and systematic commitment to cybersecurity. Strong governance is tangible proof of this commitment.
- Enabling Informed Decision-Making: Governance provides the Board of Directors and senior management with a clear view of the organization’s security posture, enabling them to make strategic decisions based on accurate data regarding risks and investments.
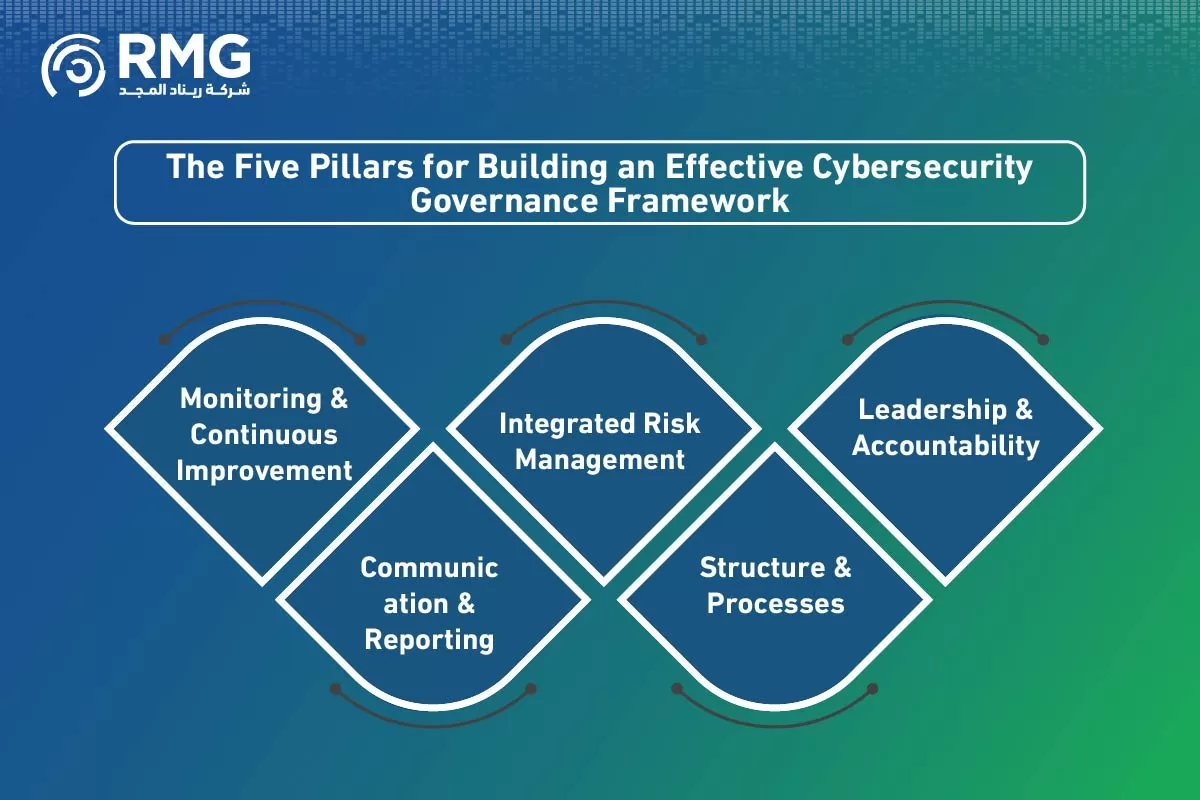
The Five Pillars for Building an Effective Cybersecurity Governance Framework
To build a robust governance system, it must be based on essential pillars that ensure its comprehensiveness and effectiveness. Understanding these pillars is the first step towards successful implementation of a cybersecurity governance program in any organization.
- Leadership & Accountability: Governance must start from the top. The Board of Directors and Executive Management bear ultimate responsibility for cybersecurity. This includes clearly defining roles and responsibilities, forming specialized committees, and ensuring an organizational culture that promotes security awareness.
- Structure & Processes: This involves designing an organizational structure that supports cybersecurity objectives, such as appointing a Chief Information Security Officer (CISO) with sufficient authority. It also includes developing and documenting policies, procedures, and standards that guide daily practices.
- Integrated Risk Management: Cyber risks cannot be separated from other business risks. The process of identifying, assessing, and addressing cyber risks must be integrated within the overarching Enterprise Risk Management (ERM) framework, ensuring a holistic and integrated view.
- Communication & Reporting: Cybersecurity governance requires effective communication channels between technical teams, senior management, and the Board of Directors. Key Performance Indicators (KPIs) and Dashboards must be developed to provide clear and concise reports on the security posture and return on investment.
- Monitoring & Continuous Improvement: Governance is not a finite project; it is a continuous cycle. Regular audits and evaluations of the effectiveness of controls and policies must be conducted, and the results used to identify weaknesses and implement necessary improvements to keep pace with evolving threats.
A Practical Roadmap for Implementing Cybersecurity Governance in Your Organization
Transitioning from theoretical understanding to practical application requires a clear methodology. Here’s a simplified roadmap that Saudi organizations can follow:
- Phase One: Assessment and Diagnosis: Start by evaluating the current situation. What are the gaps between your current practices and best practices or NCA requirements?
- Phase Two: Governance Framework Design: Based on the assessment results, design a cybersecurity governance framework tailored to your organization. Define roles, responsibilities, key policies, and decision-making mechanisms.
- Phase Three: Implementation and Activation: Begin applying the framework in practice. Train employees, disseminate new policies, and activate proposed committees and organizational structures.
- Phase Four: Monitoring and Measurement: Use the performance indicators you’ve identified to track progress and measure the effectiveness of the governance program.
- Phase Five: Review and Improvement: Periodically review the entire framework and update it based on changes in the threat environment, business objectives, or regulatory requirements.
Renad Al Majd Company: Your Strategic Partner in Building a Cybersecurity Governance System
The journey of building and implementing a cybersecurity governance system can seem complex and requires specialized expertise and a deep understanding of the local context. This is where Renad Al Majd Company (RMG) comes in, offering not just services, but a true strategic partnership. We understand that every organization in Saudi Arabia has its unique challenges and objectives. Therefore, our team of experts and consultants works alongside you to design and implement a customized governance framework that fully aligns with the requirements of the National Cybersecurity Authority (NCA) and your business goals, transforming governance from an administrative burden into a strong competitive advantage.
Towards a Secure Digital Future: Start Your Cybersecurity Governance Journey with Renad Al Majd Experts
Don’t let the complexities of cybersecurity governance hinder your organization’s path to digital excellence. Investing in a trusted partner is the fastest way to achieve compliance and build resilient and sustainable cyber defenses. Renad Al Majd Company invites all organizations, both government and private entities, in Saudi Arabia to contact our team of experts. Let us help you assess your current situation, develop a clear roadmap, and empower your leadership with the tools and insights needed to achieve effective governance that matches your ambitions. Contact us today, and let’s start building a more secure digital future for your organization together.