Blog Body
Is your organization at risk of cyber extortion? Discover its latest methods and how to build impenetrable digital defenses. This comprehensive guide is for Saudi government and private institutions that need to protect their digital assets and ensure business continuity in the face of advanced ransomware attacks.
What is Cyber Extortion and Why is it the Biggest Threat to Organizations Today?
In Saudi Arabia’s rapidly accelerating digital economy, cyber extortion has emerged as one of the most dangerous and complex challenges facing organizations of all sizes and sectors. This threat isn’t just a simple virus or a traditional hacking attempt; it’s an organized criminal operation designed to completely paralyze an organization’s operations. These criminals hold digital assets hostage in exchange for a massive ransom.
Attackers use sophisticated malware, such as ransomware, to encrypt an organization’s vital data. They also threaten to leak sensitive information about customers or employees, or even completely shut down digital services with distributed denial-of-service (DDoS) attacks. The danger of these attacks isn’t just the direct financial loss, but also their ability to destroy an organization’s reputation and erode the trust of its customers and partners. This makes cyber extortion a strategic challenge that demands an immediate and proactive response.
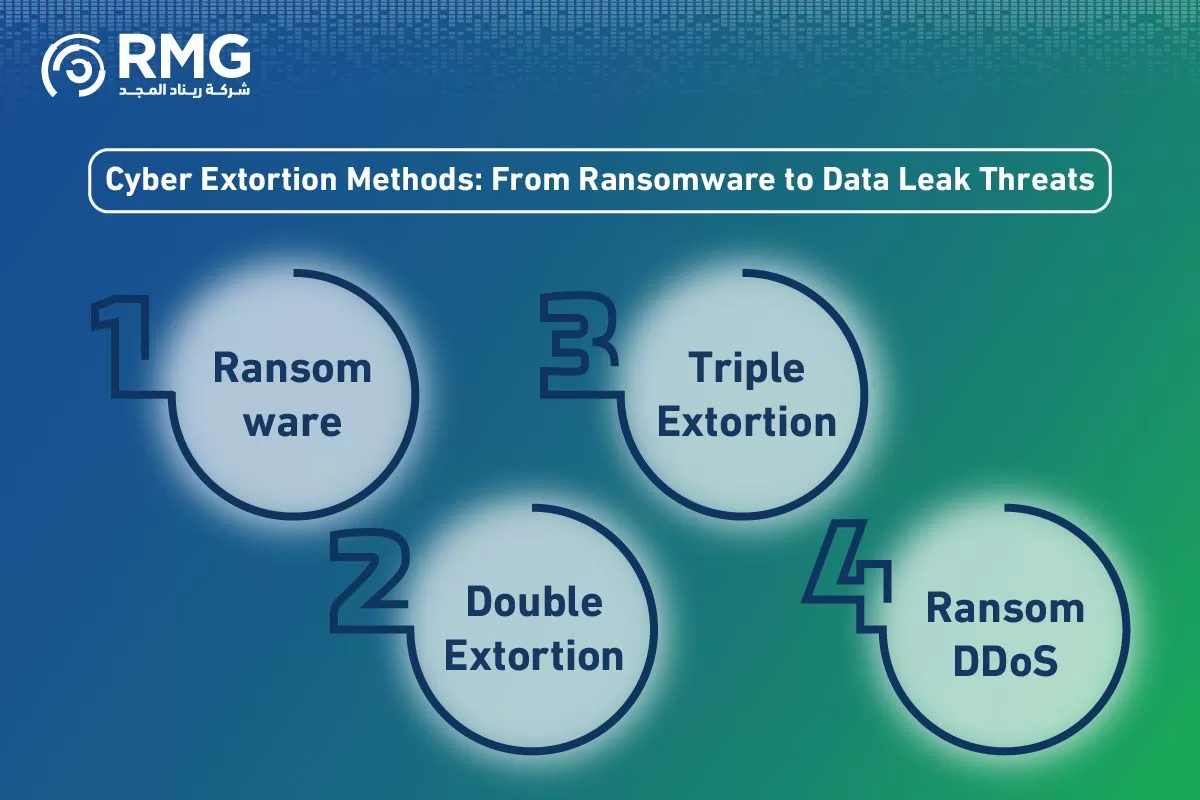
Cyber Extortion Methods: From Ransomware to Data Leak Threats
Cybercriminals’ tactics are constantly evolving, making cyber extortion methods more complex and diverse. It’s no longer just about encrypting files; it now involves multi-faceted strategies to pressure victims into paying the ransom. Some of the most prominent methods include:
- Ransomware Attacks: This is the most common method. Attackers deploy malware that encrypts all data on an organization’s servers and systems, making it inaccessible. They then demand a ransom, often in cryptocurrencies, in exchange for the decryption key.
- Double Extortion: In this method, attackers don’t just encrypt the data—they also steal a copy of it before encryption. They then threaten to publish this sensitive data on the Dark Web if the organization refuses to pay the ransom. This doubles the pressure to protect their reputation and customer data.
- Triple Extortion: This method is a dangerous escalation. In addition to encrypting and stealing data, attackers directly contact the organization’s customers, partners, or even regulatory authorities. They inform them of the breach, creating additional pressure on the target to quickly pay the ransom.
- Ransom DDoS: Here, attackers threaten to launch a massive distributed denial-of-service (DDoS) attack on an organization’s digital infrastructure. This would shut down its websites and online services unless a ransom is paid.
Understanding these diverse methods is the first step toward building effective defenses against cyber extortion threats.
Why Do Cyber Extortion Attacks Specifically Target Saudi Organizations?
The Saudi economy is experiencing tremendous growth and large-scale digital transformation, which, unfortunately, makes it an attractive target for cybercriminals. Several reasons make organizations in the Kingdom, both governmental and private, particularly vulnerable to cyber extortion attacks:
- Valuable Digital Assets: Saudi organizations hold vast amounts of valuable data, from financial information and intellectual property to the personal data of citizens and residents. This data is a treasure trove for attackers seeking quick financial gains.
- Accelerating Digital Transformation: As organizations adopt cloud technologies, the Internet of Things (IoT), and artificial intelligence (AI), their attack surface expands. This creates new vulnerabilities that attackers can exploit if not properly secured.
- Financial Ability to Pay: Attackers assume that large organizations and government entities in a strong economy like Saudi Arabia’s have the financial capacity to pay the ransom, making them high-priority targets.
- High Dependence on Digital Systems: The daily operations of both the public and private sectors in Saudi Arabia have become almost entirely dependent on digital systems. Any interruption to these systems due to a cyber extortion attack can cause widespread operational paralysis and significant losses.
The Devastating Effects of Cyber Extortion: What Lies Beyond Financial Losses
When an organization is hit by a cyber extortion attack, paying the ransom is only the tip of the iceberg. The true costs go beyond the financial amount paid to the extortionists and include devastating, long-term effects:
- Operational Losses: System shutdowns completely disrupt operations, preventing the organization from providing services or producing goods, resulting in direct revenue losses.
- Reputation Damage and Loss of Trust: Announcing a data breach or an organization’s inability to protect its digital assets erodes the trust of customers, partners, and investors. These are intangible assets that are difficult to recover.
- Recovery and Response Costs: These costs include expenses for digital forensics investigations, rebuilding systems from scratch, improving cybersecurity infrastructure, and legal consultation fees.
- Regulatory and Legal Penalties: Organizations may face hefty fines from regulatory bodies, such as the National Cybersecurity Authority, for failing to protect data, in addition to potential lawsuits from affected parties.
- Permanent Data Loss: Even after paying the ransom, there’s no guarantee that attackers will provide the correct decryption key, or that the recovered data won’t be corrupted or stolen.
Proactive Defense Strategies: Building an Impenetrable Fortress Against Cyber Extortion
Dealing with cyber extortion doesn’t start when the attack happens; it starts with building a proactive security culture, policies, and procedures. Effective defense requires a multi-layered approach that includes:
- Continuous Employee Awareness and Training: Employees are the first line of defense. They should be regularly trained on how to recognize phishing emails, avoid suspicious links and attachments, and the importance of using strong passwords.
- Robust and Isolated Backups: Organizations must implement a 3-2-1 backup strategy: have three copies of the data, on two different types of storage media, with at least one copy in a separate, offline/air-gapped location.
- Applying the Principle of Least Privilege: Employees and systems should only be granted the access privileges they need to perform their jobs. This limits the scope of damage if a user’s account is compromised.
- Continuous Updates and Vulnerability Management: Security updates for systems, software, and applications must be applied as soon as they’re released to patch known vulnerabilities that attackers exploit.
- Using Advanced Security Solutions: This includes next-generation firewalls (NGFW), intrusion detection and prevention systems (IDPS), advanced endpoint protection solutions (EDR), and tools for analyzing user and network behavior.
Renad Al-Majd: Your Strategic Partner in Averting Cyber Extortion Risks
In the face of this complex threat landscape, organizations can’t rely on traditional solutions alone. Countering cyber extortion requires specialized expertise and a strategic partner who deeply understands the nature of these attacks and the Saudi market. This is where Renad Al-Majd (RMG) comes in. We position ourselves as an advanced line of defense and a trusted partner for government and private institutions in the Kingdom.
Renad Al-Majd’s services aren’t just limited to selling security products; we provide comprehensive consultations and customized solutions. We start by assessing your current security posture, identifying weaknesses, and then design and implement a resilient cybersecurity infrastructure capable of withstanding the most complex attacks. Our expert team has a deep understanding of attackers’ tactics, which allows us to build proactive defenses that protect your organization before any damage occurs.
Towards a Secure Digital Future: How Renad Al-Majd Leads Your Organization’s Digital Fortification Journey
Investing in cybersecurity is no longer an option—it’s a necessity to ensure business continuity and protect national assets. Renad Al-Majd invites all government and private institutions in Saudi Arabia to adopt a proactive approach to facing cyber extortion.
By partnering with us, you get more than just a service; you get a partner committed to securing your digital transformation journey. Our integrated services include:
- Comprehensive cybersecurity risk assessment.
- Developing and implementing incident response plans.
- Building advanced Security Operations Centers (SOCs).
- Customized awareness and training programs for your employees.
- Providing the latest global security technologies and solutions.
Don’t wait to become the next victim. Contact the experts at Renad Al-Majd today to start a strategic conversation about how to build a secure and fortified digital future for your organization and contribute to a trustworthy and safe digital environment in the Kingdom.