Blog Body
Discover how cyber attack analysis can fortify your organization’s defenses in Saudi Arabia. Learn the stages, tools, and the importance of transforming attack data into proactive security strategies to protect your digital assets today.
In the rapidly evolving digital landscape of the Kingdom of Saudi Arabia, cyber attacks are no longer just potential threats—they are a reality that demands precise readiness and a scientific methodology. This is where cyber attack analysis emerges as a vital process that isn’t limited to understanding what happened after a breach; it extends to become a cornerstone for building resilient defenses capable of predicting and deterring future threats. This analysis is not merely a technical procedure; it’s an art and a science aimed at dissecting the attack, understanding the motives of the attackers, and accurately identifying attack vectors. This empowers government and private institutions to transform a painful breach experience into an unprecedented opportunity to strengthen their digital infrastructure.
Why is Cyber Attack Analysis a Cornerstone of the Kingdom’s Digital Security Strategy?
In Saudi Arabia’s business environment, which is aggressively moving toward digital transformation, the value of digital assets increases daily, making them more attractive to attackers. Cyber attack analysis doesn’t just aim to determine the damage; it provides immense strategic value to organizations. Its importance lies in the following points:
- Understanding Attacker Tactics, Techniques, and Procedures (TTPs): Deep analysis allows for an understanding of the methods, tactics, and procedures that attackers follow. This helps in building proactive defenses specifically designed to counter certain types of threats that target critical sectors in the Kingdom.
- Strengthening Defensive Weaknesses: By dissecting the attack, analysis reveals the security vulnerabilities that were exploited, whether technical (like unpatched software) or human (like phishing). This allows for immediate and permanent remediation.
- Preventing Similar Attacks from Recurring: The most important lesson learned from any attack is how to prevent it in the future. Cyber attack analysis provides clear insights that translate into new security policies, procedures, and controls to prevent attackers from using the same paths again.
- Improving Incident Response Speed: When a cybersecurity team understands how previous attacks occurred, they become more efficient at detecting and handling future attacks quickly and effectively, which reduces downtime and potential damages.
- Regulatory and Legislative Compliance: Regulatory bodies in the Kingdom, such as the National Cybersecurity Authority (NCA), enforce strict incident reporting requirements. Accurate and systematic cyber attack analysis is fundamental for preparing these reports and meeting compliance requirements.
Cyber Attack Analysis Stages: An Integrated Methodology to Uncover the Threads of a Breach
To ensure maximum benefit from the analysis process, a structured methodology consisting of several integrated stages is followed. Adhering to these stages ensures that no vital evidence is overlooked and helps build a complete and accurate picture of the attack’s timeline.
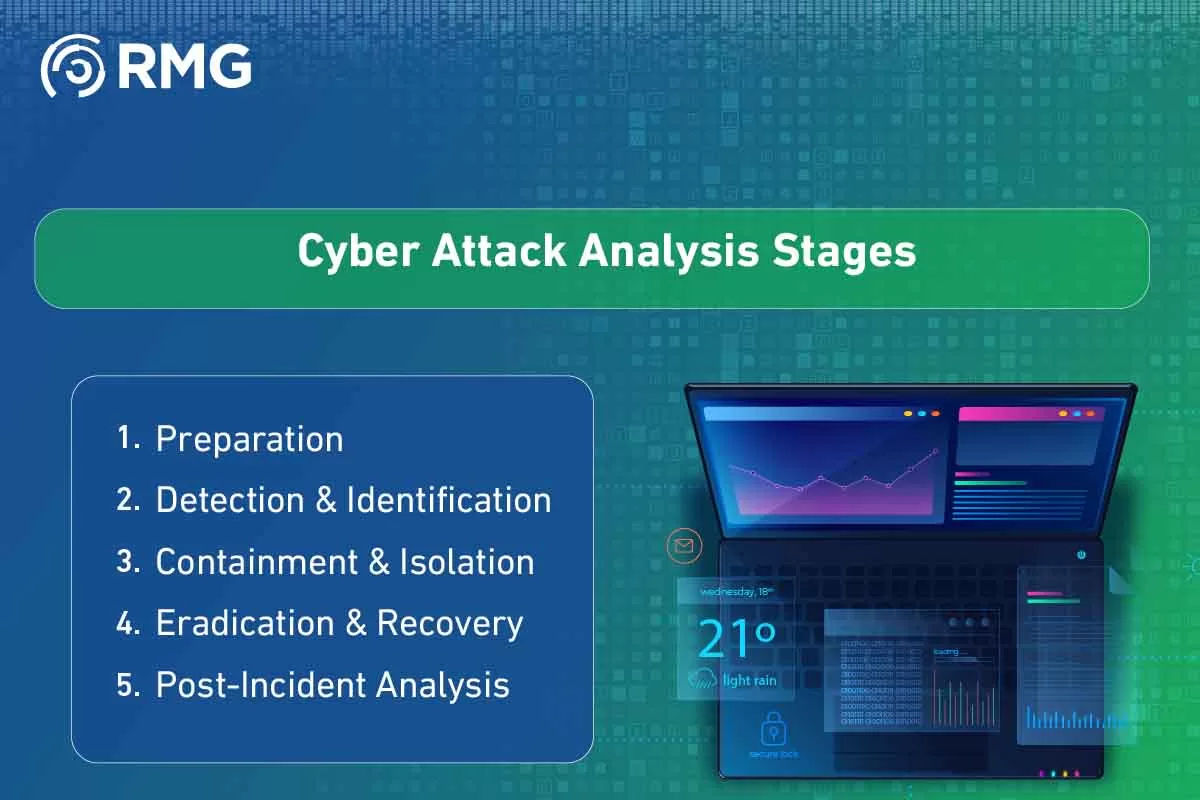
- Preparation: Before any attack occurs, an organization must be ready. This stage includes building a Computer Incident Response Team (CIRT), defining roles and responsibilities, preparing the necessary tools for collecting digital evidence, and establishing clear communication plans. Good preparation is half the battle in the world of cyber attack analysis.
- Detection & Identification: This is the actual starting point of the analysis. In this stage, suspicious activity is detected through various monitoring systems (such as SIEM, IDS/IPS), and it is determined whether this activity constitutes a real security incident. The severity of the incident and its initial impact on the organization’s systems are then assessed.
- Containment & Isolation: Once an attack is confirmed, the top priority is to prevent it from spreading and causing more damage. This stage involves isolating affected systems from the network, disabling compromised user accounts, or applying temporary firewall rules. This step is crucial in cyber attack analysis to limit losses.
- Eradication & Recovery: After containing the threat, the process of completely eliminating it from the systems begins. This includes removing malware, patching the exploited vulnerabilities, and ensuring there are no backdoors left by the attacker. Afterward, systems and data are safely restored from clean backups and returned to service.
- Post-Incident Analysis: This is the most strategic stage of the cyber attack analysis process. Here, the team conducts a deep analysis of all the collected evidence to answer fundamental questions: How did the attack start? Which systems were affected? What data was accessed or exfiltrated? What weaknesses allowed the attack to happen? All this information is documented in a detailed report that includes practical recommendations for preventing future incidents.
Advanced Tools and Techniques in Cyber Attack Analysis
The effectiveness of analysis largely depends on the tools and techniques used. Without the right tools, collecting and interpreting evidence becomes a nearly impossible task. Among the most prominent tools are:
- Security Information and Event Management (SIEM) Systems: These systems collect and analyze logs from various network and system sources in real time to detect suspicious patterns and correlations that may indicate an attack.
- Digital Forensics Tools: These specialized tools are used to examine hard drives and RAM for remnants of malicious activity, recover deleted files, and analyze malware.
- Threat Intelligence Platforms: These platforms provide up-to-date information on the latest threats, attackers, and their tactics. Integrating this information into cyber attack analysis helps link a local incident to broader global attack campaigns.
- Network Detection and Response (NDR) Solutions: These solutions continuously monitor network traffic to identify anomalous behaviors that might bypass traditional defenses, providing crucial visibility during analysis.
Renad Al-Majd (RMG): Your Strategic Partner in Cyber Attack Analysis and Digital Resilience
Understanding the complexities of cyber attack analysis requires deep expertise, advanced techniques, and a precise understanding of the threat landscape facing Saudi organizations. At Renad Al-Majd (RMG), we don’t just provide services; we build a strategic partnership with our government and private sector clients to fortify their digital defenses. Our team of certified experts has the advanced tools and methodologies needed to dissect the most complex attacks and provide actionable insights that transform security challenges into opportunities for safe and sustainable growth. We recognize that every organization in the Kingdom has unique needs, which is why we tailor our cyber attack analysis services to align with your strategic objectives and operational requirements.
Elevate Your Cybersecurity to New Heights: Start Your Journey with Renad Al-Majd Experts Today
Don’t wait for the next attack to realize the importance of preparation. Investing in cyber attack analysis capabilities today is an investment in your business continuity, reputation, and digital future. Renad Al-Majd (RMG) invites you to collaborate with us and benefit from our extensive experience in cybersecurity. Whether you need to build incident response capabilities from scratch, conduct a deep analysis of a recent incident, or simply enhance your proactive defenses, our team is fully prepared to provide support and advice. Contact us today to begin building a formidable digital shield that protects your most valuable assets and ensures you achieve your goals in a secure and reliable digital environment.