Blog Body
Discover how the latest cybersecurity technologies can form your first line of defense against digital threats. A specialized guide for Saudi organizations to effectively protect their vital assets and strengthen their digital infrastructure.
In the digital age of Saudi Arabia, where the pace of digital transformation is accelerating across all governmental and private sectors, cybersecurity is no longer an option—it has become a strategic necessity. Protecting information assets and critical infrastructure from sophisticated attacks requires a deep understanding and precise application of the latest technologies in this field. This article sheds direct and intensive light on the key cybersecurity technologies that every organization in the Kingdom should adopt to ensure business continuity and digital sovereignty.
Next-Generation Firewalls (NGFW): The First Guardian of Your Network
Next-Generation Firewalls (NGFWs) represent a revolutionary evolution from traditional firewalls. Their function is not limited to inspecting ports and data packets; they go beyond that to provide deep content and application inspection capabilities. This technology gives organizations a comprehensive view of activities within their networks, allowing them to enforce precise security policies based on user identity and application type, not just on IP addresses. By integrating Intrusion Prevention Systems (IPS) and application control, these cybersecurity technologies form the first and most critical line of defense against both external and internal threats.
Intrusion Detection and Prevention Systems (IDPS): The Vigilant Radar Against Suspicious Activity
Intrusion Detection and Prevention Systems (IDPS) act as a watchful eye, monitoring network traffic and system activities for any malicious or unauthorized behavior. These systems use advanced methods such as signature-based analysis to identify known attacks and anomaly-based analysis to pinpoint abnormal activities that may indicate a new or zero-day attack. When a threat is detected, these systems can log it, send an alert to administrators, or take proactive measures to immediately block the attack, making them a vital component of a deep defense strategy.
Advanced Encryption Technologies: Protecting Data at Rest and In Transit
Data is the core of any organization, and its protection is non-negotiable. This is where advanced encryption technologies come in. Advanced encryption ensures that sensitive data is converted into an unreadable format, accessible only to authorized parties. Encryption should be applied to data in all its states:
- Data in Transit: Using protocols like TLS/SSL to protect data as it travels across public and private networks.
- Data at Rest: Encrypting databases, files stored on servers, and hard drives to protect them from unauthorized access, even in the event of a physical server breach.
Data Loss Prevention (DLP) Solutions: Complete Control Over Your Sensitive Information
Data Loss Prevention (DLP) solutions go beyond simply protecting data from external theft; they focus on preventing accidental or intentional leakage by internal users. These cybersecurity technologies work by monitoring, classifying, and controlling sensitive data (such as customer information, intellectual property, and financial records). DLP policies can prevent users from printing, copying, or sending sensitive data via email, instant messaging applications, or portable storage devices, providing a critical layer of protection against insider threats.
Identity and Access Management (IAM): Who Holds the Keys to Your Digital Kingdom?
Identity and Access Management (IAM) is a cornerstone of ensuring that only the right people have access to the right resources at the right time. IAM solutions are based on key principles such as:
- Multi-Factor Authentication (MFA): Adding an extra layer of security that requires more than just a password to verify a user’s identity.
- Principle of Least Privilege: Granting users the minimum privileges necessary to perform their functions and nothing more.
- Identity Lifecycle Management: Automating the processes of creating, modifying, and deactivating user accounts to ensure there are no “orphaned” or inactive accounts that could pose a security vulnerability.
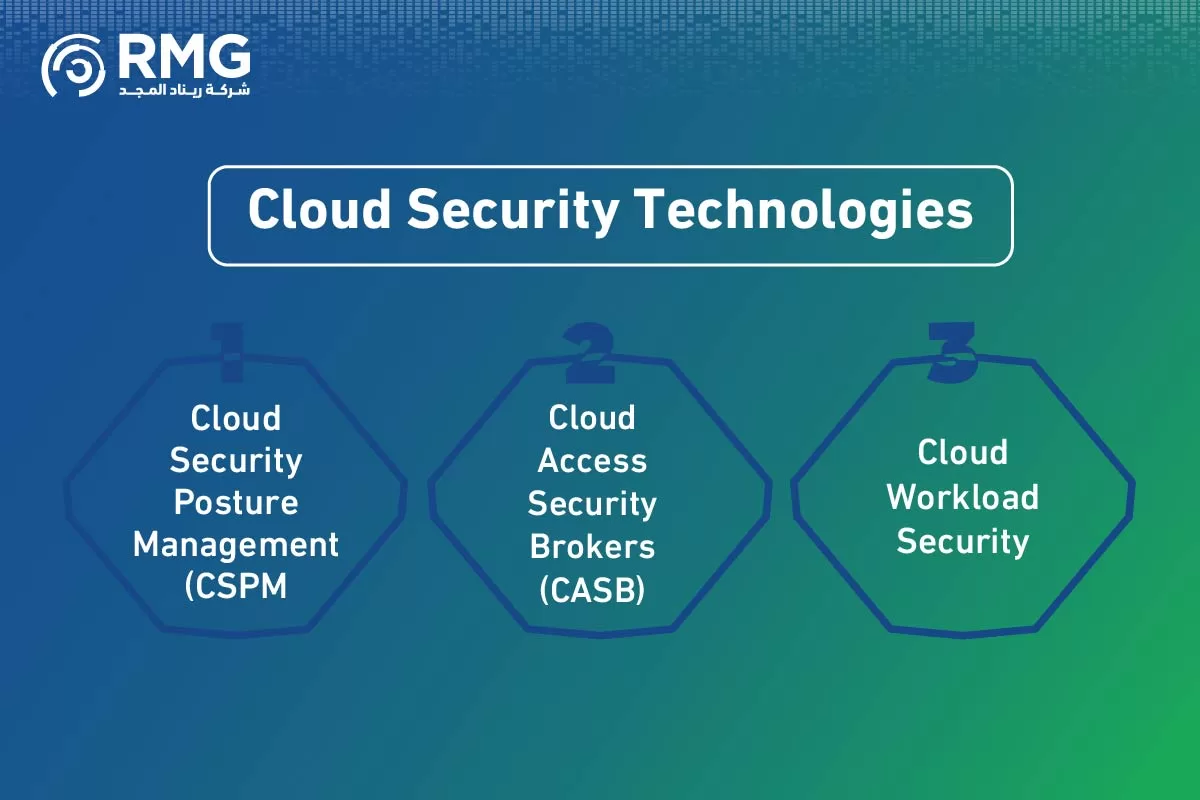
Cloud Security Technologies: Protecting Assets in Virtual Environments
With the widespread adoption of cloud computing in the Kingdom, cloud security has become a standalone specialty within cybersecurity technologies. Cloud security covers the protection of data, applications, and infrastructure hosted on platforms like AWS, Azure, and Google Cloud. Key technologies here include:
- Cloud Security Posture Management (CSPM): Tools that scan cloud environments for misconfigurations that could lead to security vulnerabilities.
- Cloud Access Security Brokers (CASB): Solutions that act as a control point between users and cloud service providers to enforce security policies.
- Cloud Workload Security: Protecting virtual servers, containers, and applications running in the cloud.
Artificial Intelligence and Machine Learning: The Future of Proactive Cyber Defense
The integration of Artificial Intelligence (AI) and Machine Learning (ML) into cybersecurity technologies represents a paradigm shift from reactive to proactive and predictive defense. These technologies can analyze vast amounts of security data in real time to identify complex patterns and anomalies that might escape traditional tools. By learning normal network behavior, AI can detect new and unknown threats, predict potential attacks before they happen, and automate incident response faster and more efficiently than human intervention.
IoT Security: The Challenge of Protecting Connected Devices
With the proliferation of smart cities and mega-projects in the Kingdom, the number of IoT devices is growing exponentially, and every connected device represents a potential entry point for attackers. IoT security requires a multi-layered approach that includes:
- Network Segmentation: Isolating IoT devices on a separate network to prevent any breach from spreading to an organization’s critical networks.
- Device Lifecycle Management: Securing devices from the manufacturing stage to their end-of-life, including regular firmware updates.
- Strong Device Authentication: Verifying the identity of each device before allowing it to connect to the network.
Renad Al Majd Company: Your Strategic Partner for Adopting the Latest Cybersecurity Technologies
Understanding these technologies is the first step, but implementing and effectively integrating them into a complex work environment requires deep expertise and a reliable partner. This is where Renad Al Majd Company (RMG) comes in, putting its extensive experience and team of certified experts at the service of organizations and government and private entities in the Kingdom. We don’t just provide off-the-shelf solutions; we act as a strategic partner to understand your unique challenges, assess your current infrastructure, and design and implement a comprehensive cybersecurity strategy based on the best and latest cybersecurity technologies mentioned. We ensure that our solutions are fully compliant with local regulatory frameworks and the standards of the National Cybersecurity Authority, giving you the confidence and peace of mind to focus on growing your business.
Towards a Secure Digital Future: Start Your Journey with Renad Al Majd Experts Today
Investing in cybersecurity technologies is an investment in the stability and future of your organization. Don’t let your organization be the next target. Renad Al Majd Company invites you to start a strategic dialogue on how to secure your digital assets and build resilient cyber defenses capable of facing tomorrow’s challenges. Contact our team of specialized consultants today for a comprehensive assessment and discover how our partnership can transform your cybersecurity challenges into a true competitive advantage, ensuring you achieve your goals in a safe and reliable digital environment.